Utilizing Morse Code to Evade Signature Based Detection Systems
Por um escritor misterioso
Descrição

This 'unique' phishing attack uses Morse code to hide its approach
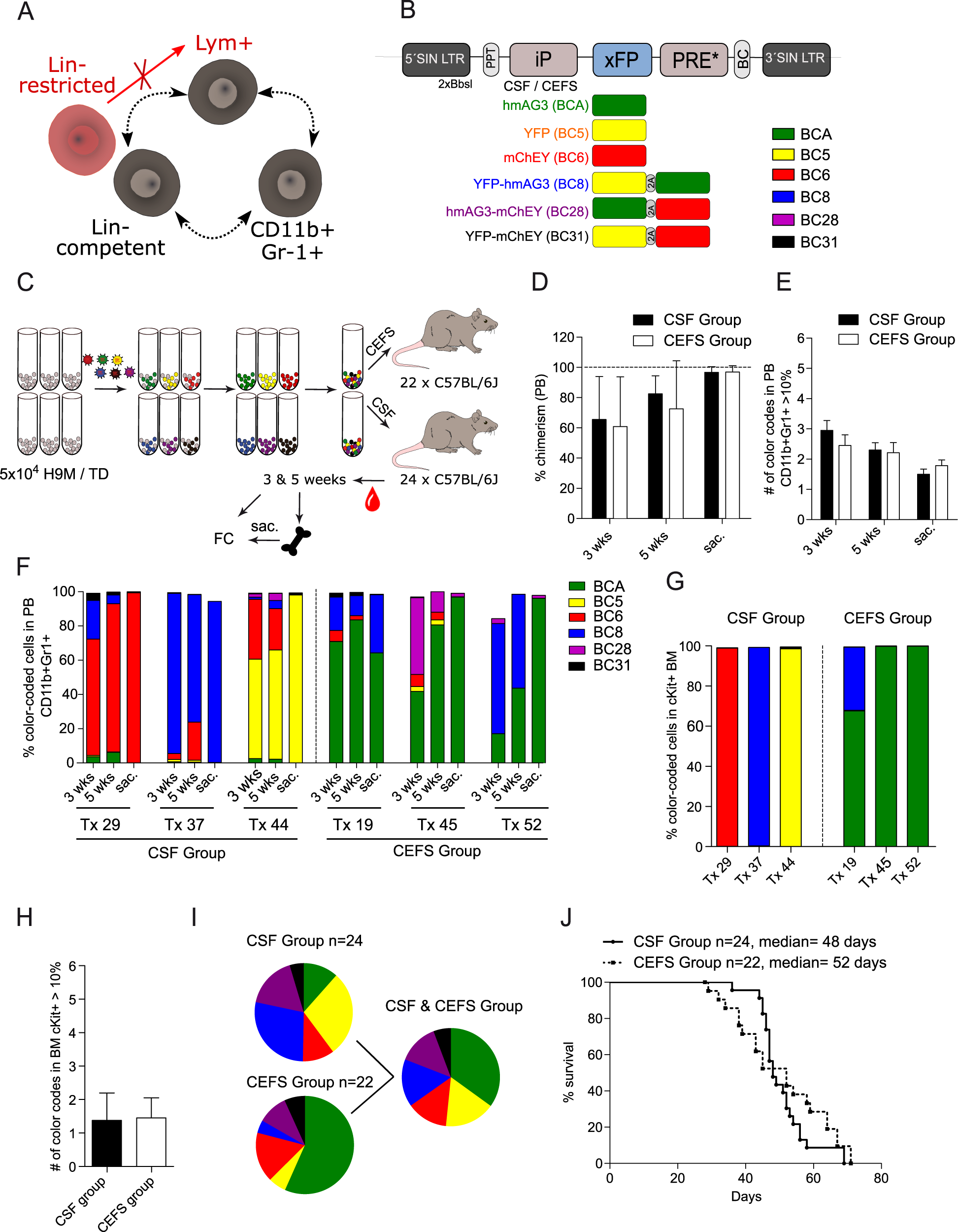
A pro B cell population forms the apex of the leukemic hierarchy in Hoxa9/Meis1-dependent AML
Conception of recoding the international Morse code for information

Hackers are Using Morse Code to Avoid Detection - IDStrong

Volume 2-issue-6-2037-2039

Morse Code Ninja

Public Secret Message - TV Tropes

Threat Intelligence Report for August 9 - 15, 2021
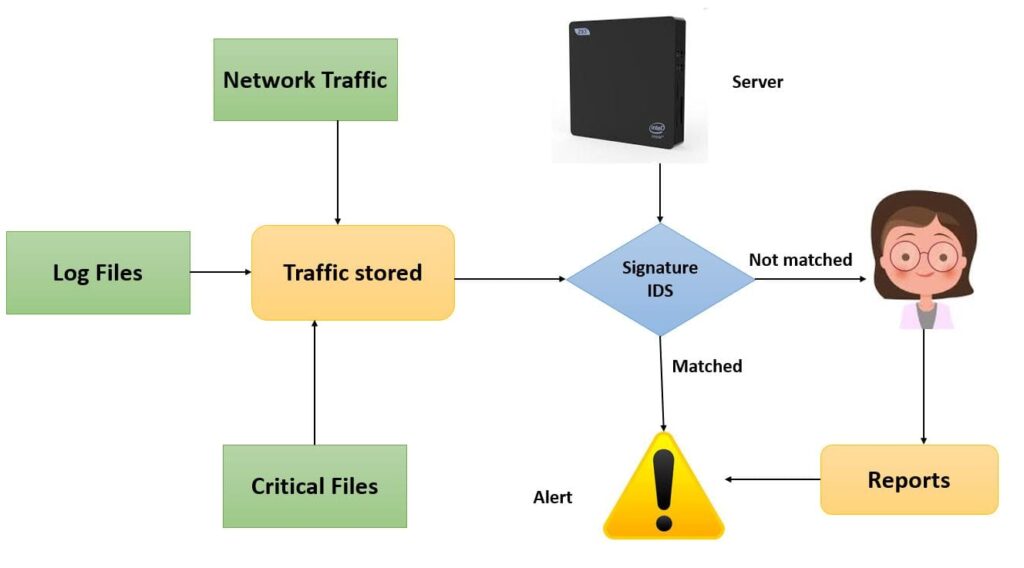
What is Intrusion Detection System [IDS]? - UseMyNotes

Attackers use Morse code, other encryption methods in evasive phishing campaign

Applied Sciences, Free Full-Text
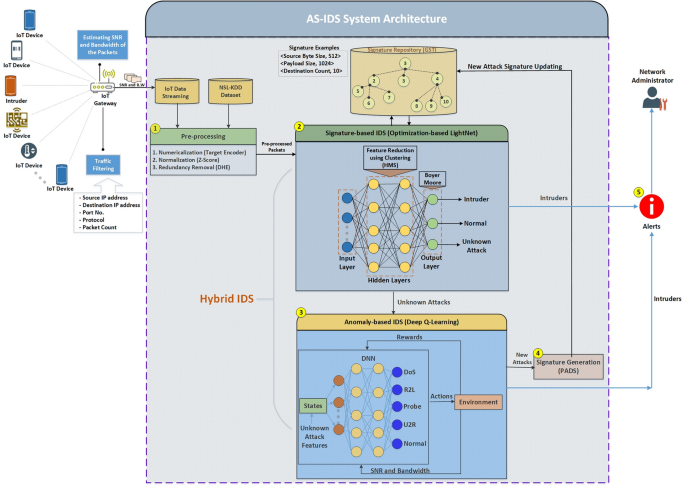
AS-IDS: Anomaly and Signature Based IDS for the Internet of Things

PDF] Morse code based Secured Authentication System using Eye Blink through Haar Cascade and Facial Landmark Algorithm

CEH (VII): System Hacking

PDF] Morse code based Secured Authentication System using Eye Blink through Haar Cascade and Facial Landmark Algorithm
de
por adulto (o preço varia de acordo com o tamanho do grupo)