Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
Por um escritor misterioso
Descrição
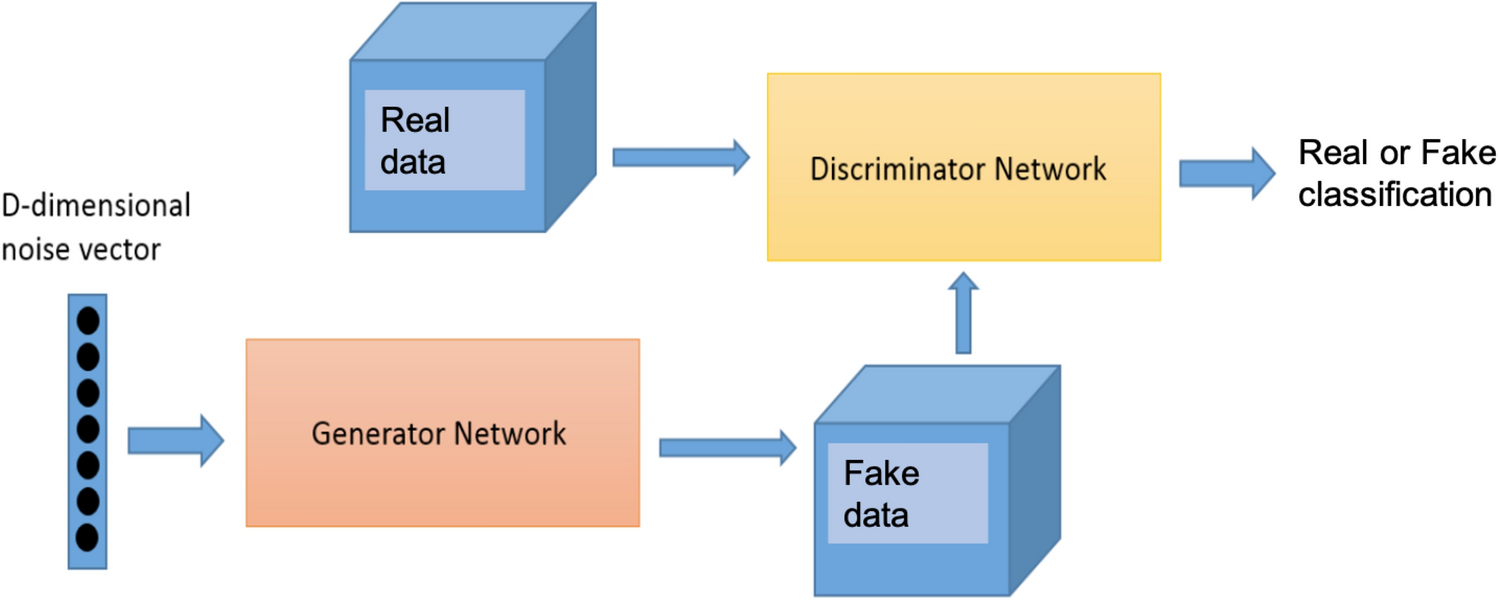
Synthetic flow-based cryptomining attack generation through Generative Adversarial Networks
Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
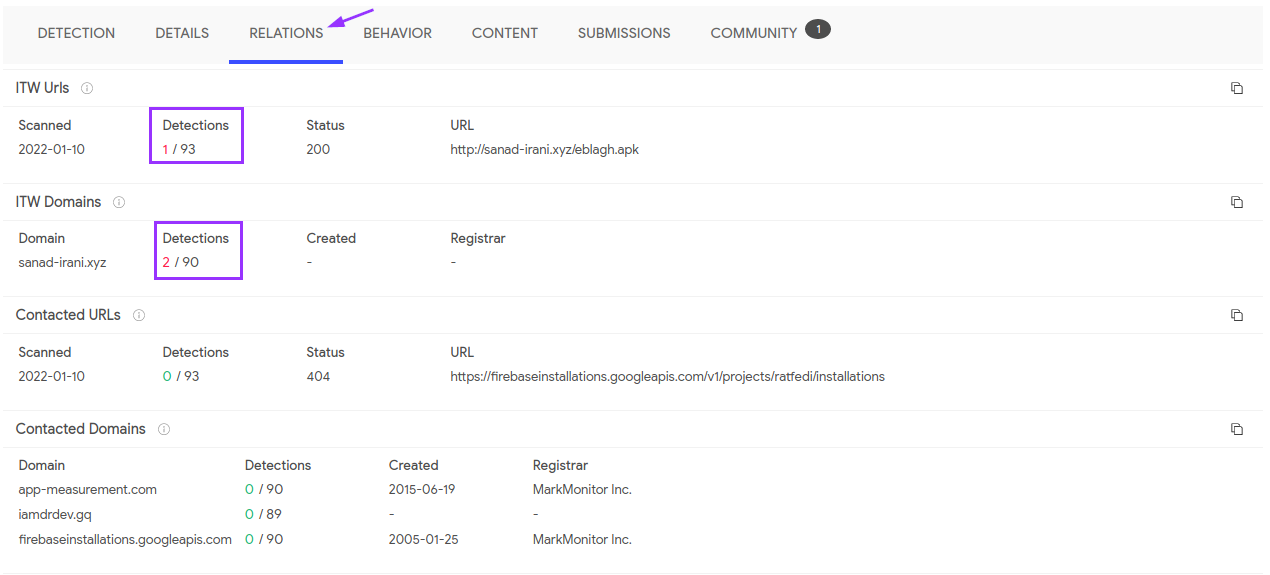
Real-world Android Malware Analysis 1: eblagh.apk

A Survey of Binary Code Fingerprinting Approaches: Taxonomy, Methodologies, and Features

424B4

Disarming visualization-based approaches in malware detection systems - ScienceDirect

IT threat evolution Q2 2020. PC statistics - vulnerability database

A Review on Malware Analysis for IoT and Android System
PDF) A Survey of Android Malware Static Detection Technology Based on Machine Learning
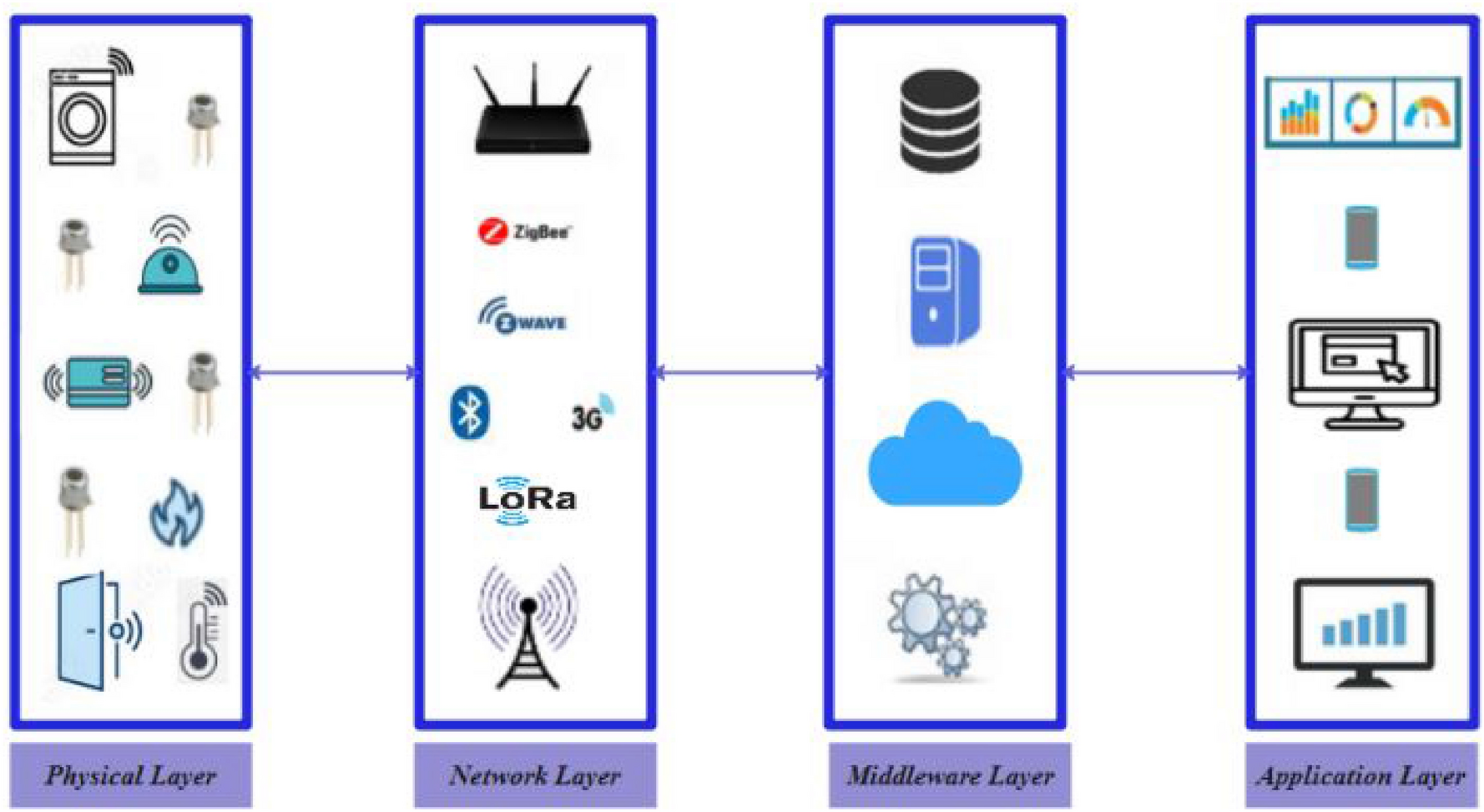
A survey on performance evaluation of artificial intelligence algorithms for improving IoT security systems
de
por adulto (o preço varia de acordo com o tamanho do grupo)