Cryptojacking: Understanding and defending against cloud compute
Por um escritor misterioso
Descrição
The Silent Threat of Cryptojacking and How to Protect Yourself

What is Cryptojacking? - Syntax Technologies
The Silent Threat of Cryptojacking and How to Protect Yourself
What Is Cryptocurrency Mining? How to Prevent Cryptojacking? - Huawei

Cybersecurity Attacks 101: Phishing, Cryptojacking and Ransomware
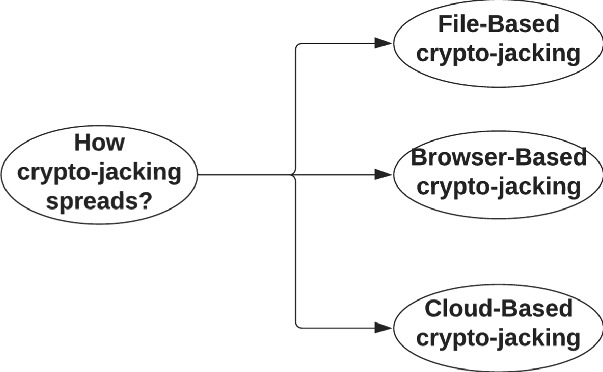
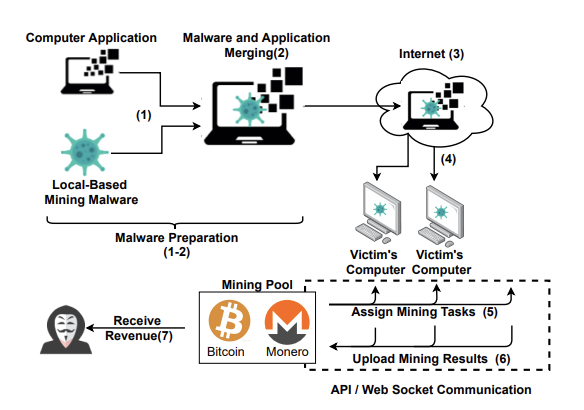
Variants of Crypto-Jacking Attacks and Their Detection Techniques
Detect cryptojacking with Sysdig's high-precision machine learning
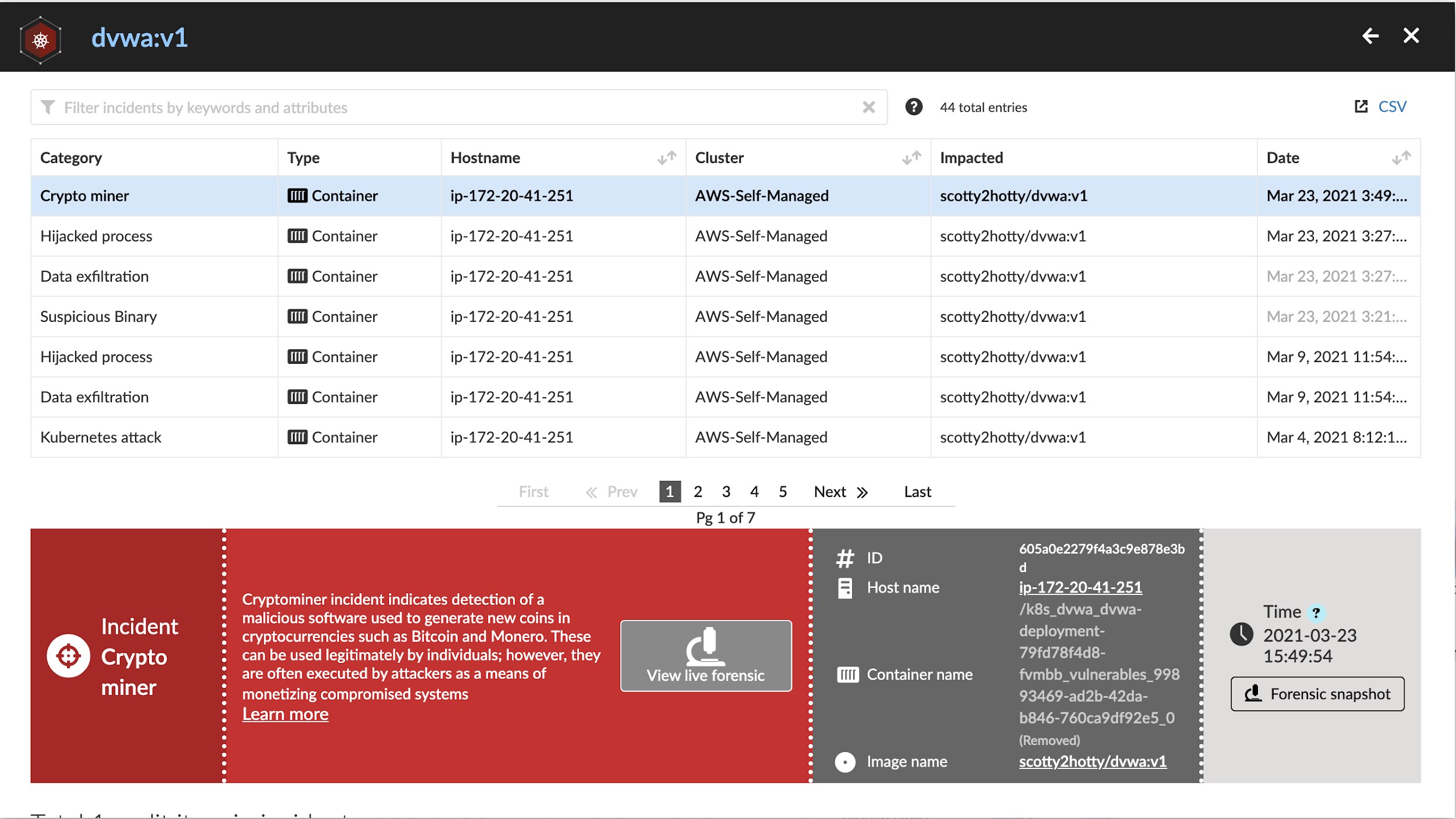
WAAS-Up with Cryptojacking Microservice-Based Web Apps?

Top 10 Cloud Attacks and What You Can Do About Them - Aqua
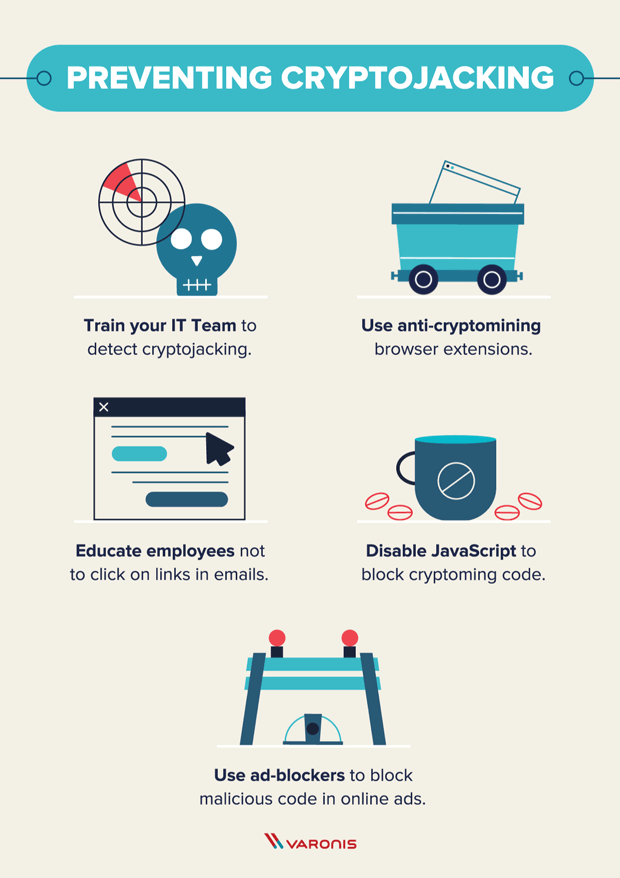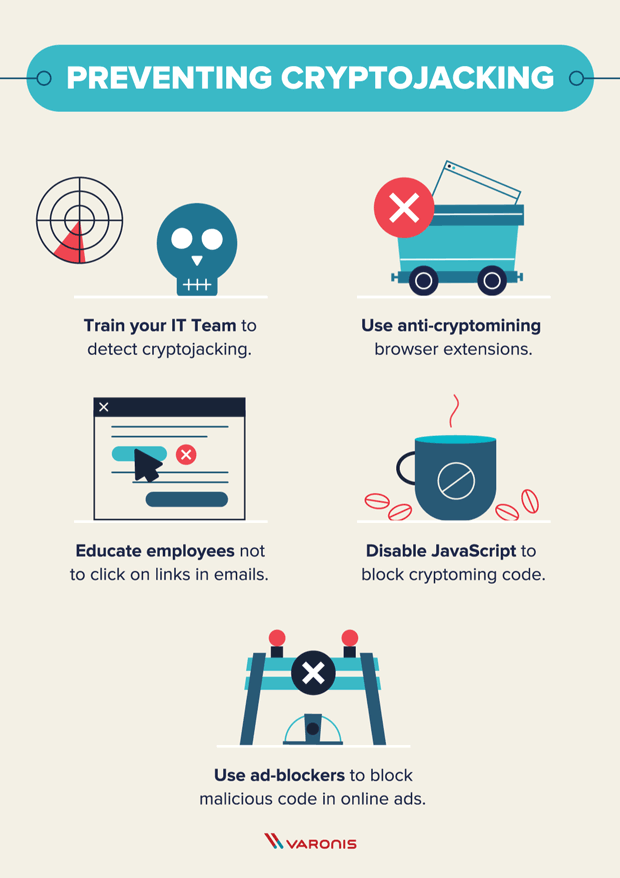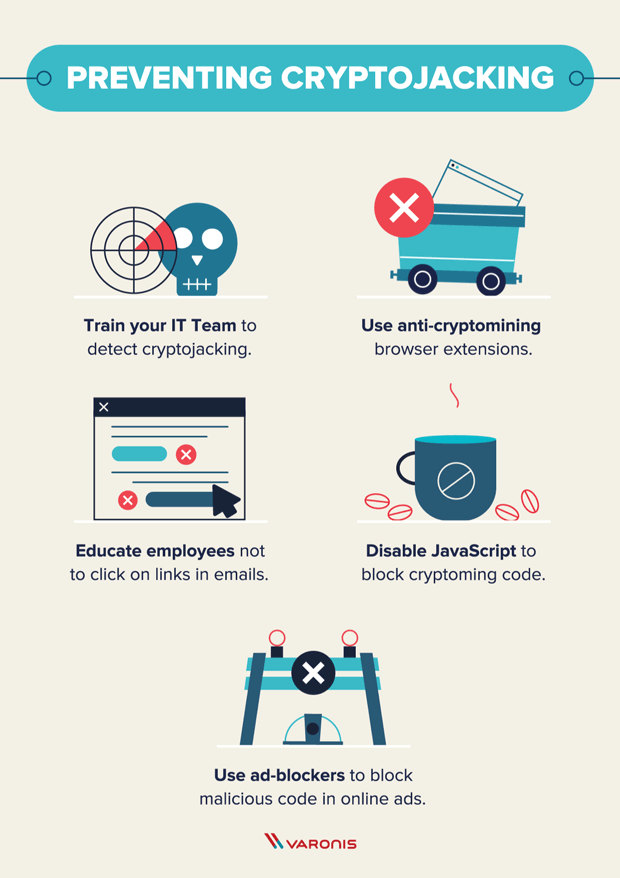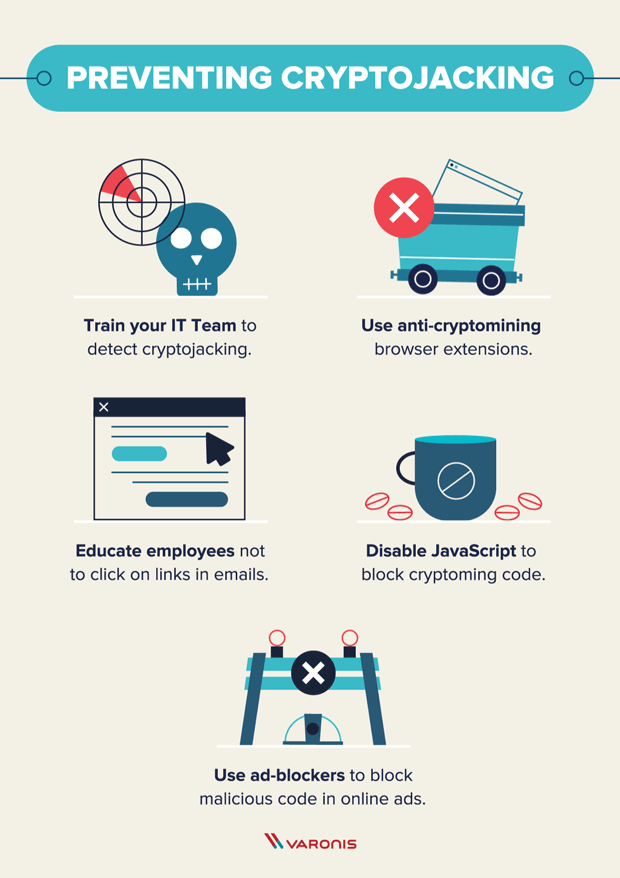
What Is Cryptojacking? Prevention and Detection Tips

Cryptojacking Attacks: Who's Mining on Your Coin?
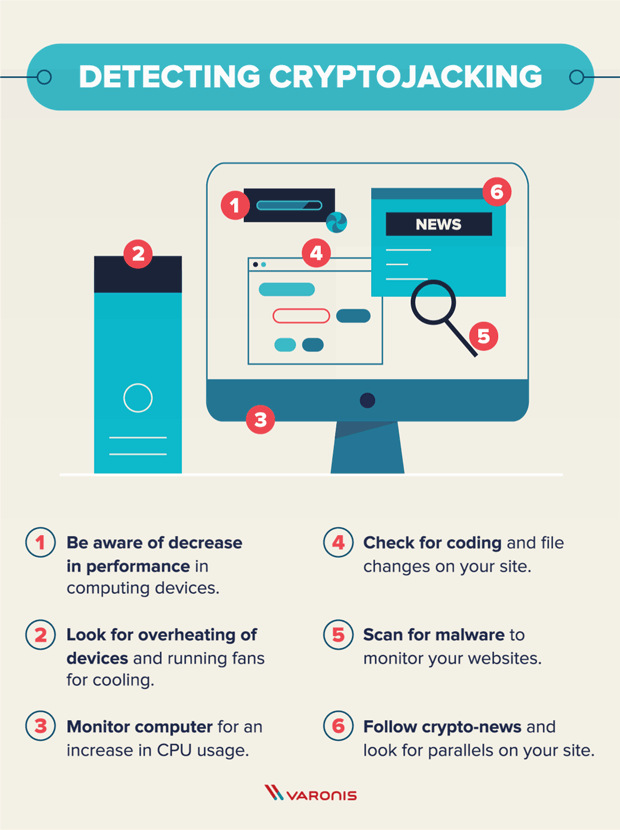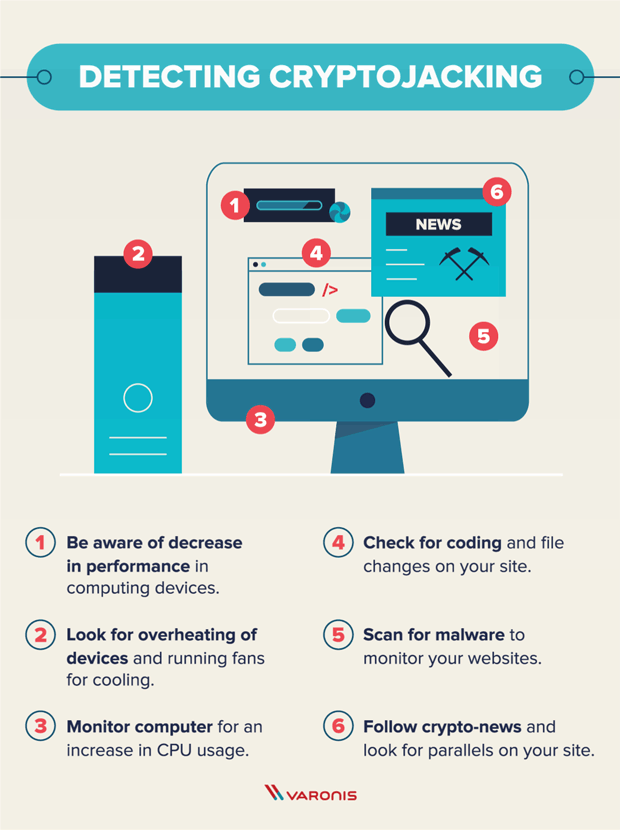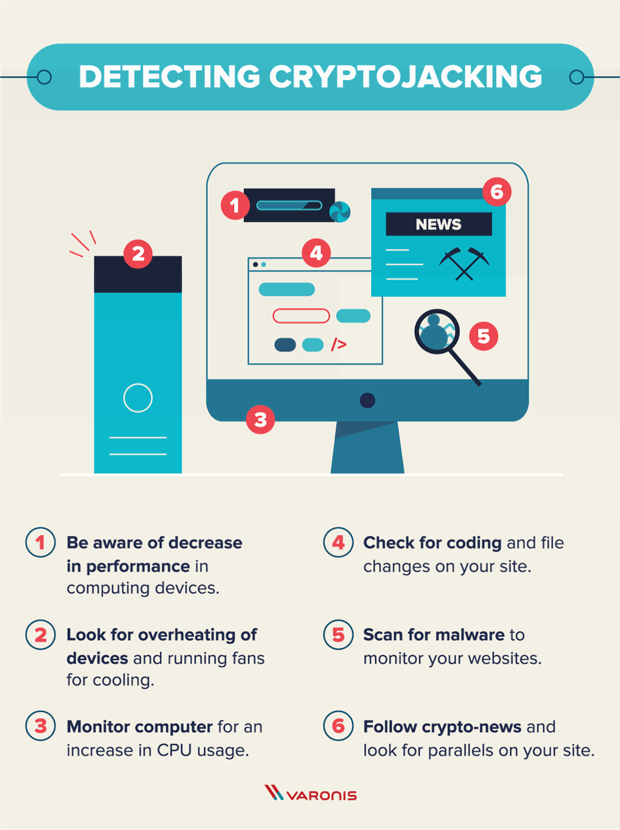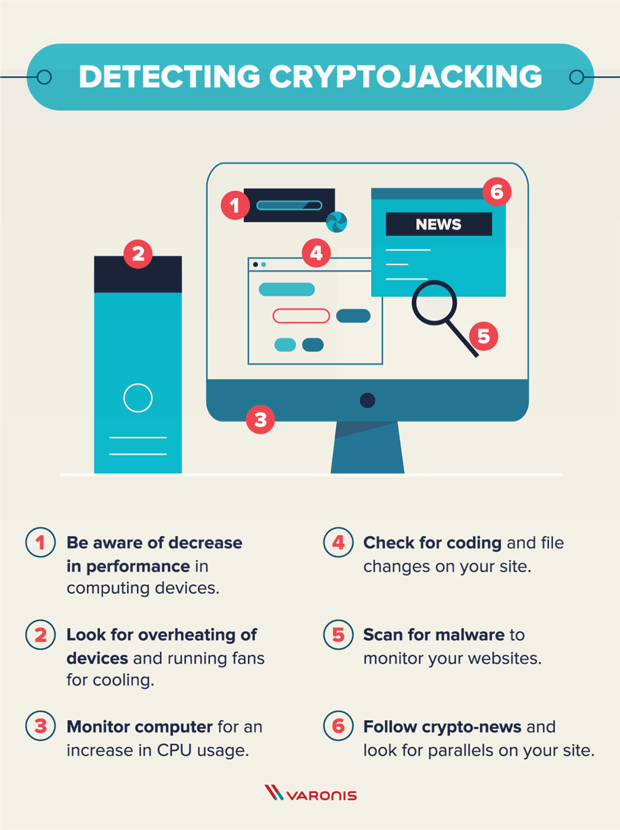
What Is Cryptojacking? Prevention and Detection Tips

Cryptojacking: Understanding and defending against cloud compute

Cryptojacking Azure, Storm-0558, Microsoft 365 Copilot News

What Is Cryptojacking: Examples and How to Prevent It?
de
por adulto (o preço varia de acordo com o tamanho do grupo)