Delay-CJ: A novel cryptojacking covert attack method based on
Por um escritor misterioso
Descrição
Cryptojacking is a type of resource embezzlement attack, wherein an attacker secretly executes the cryptocurrency mining program in the target host to…
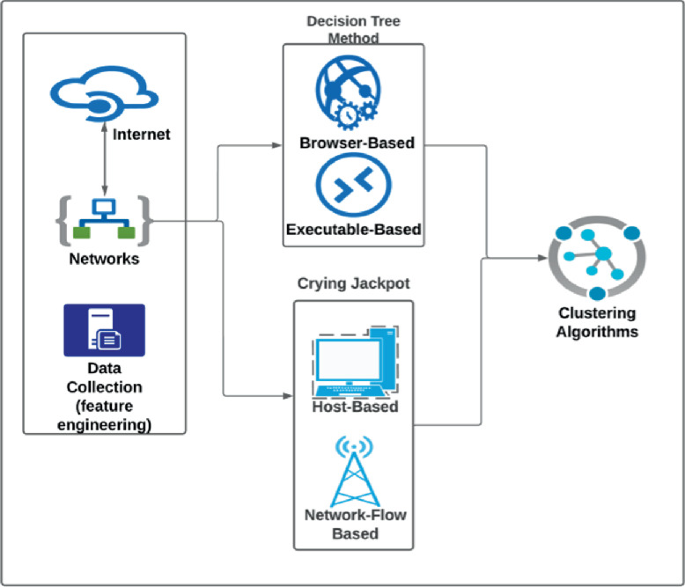
Variants of Crypto-Jacking Attacks and Their Detection Techniques
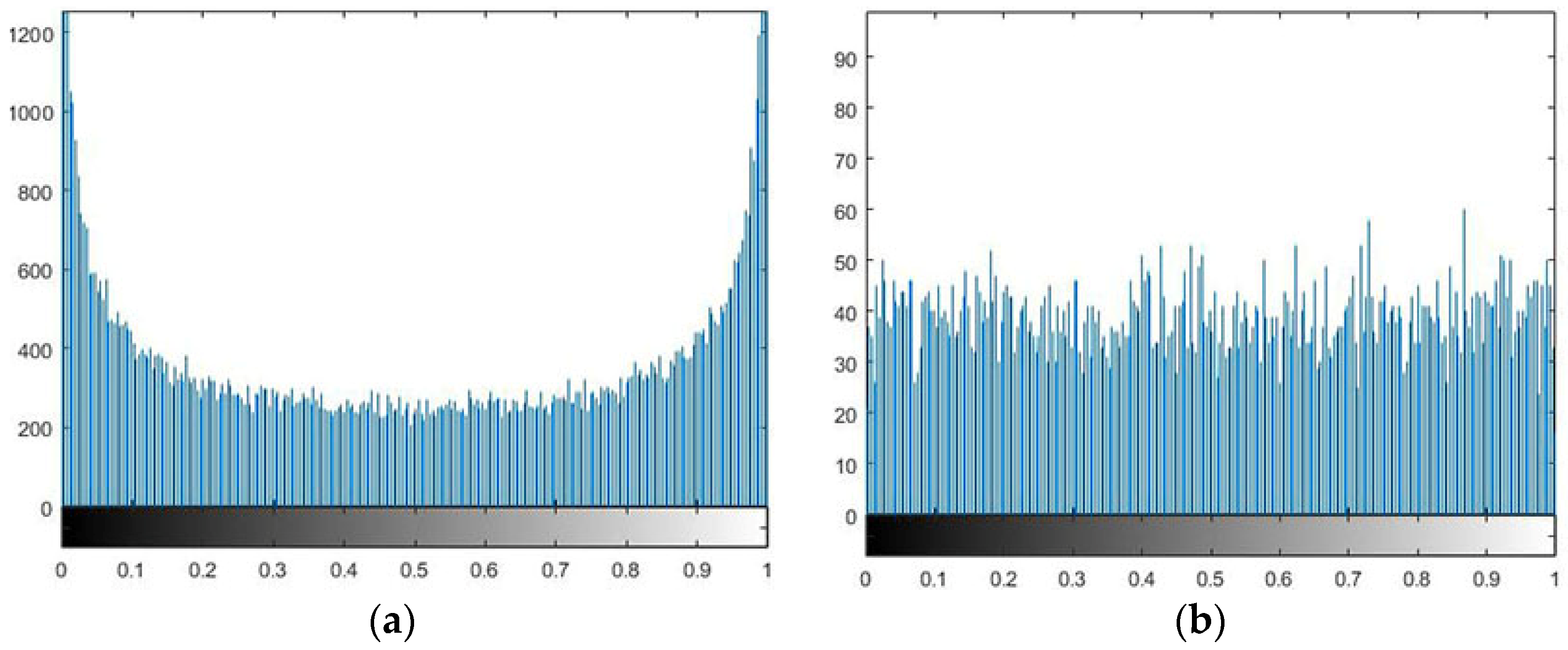
Electronics, Free Full-Text

Full article: Cryptojacking injection: A paradigm shift to cryptocurrency- based web-centric internet attacks
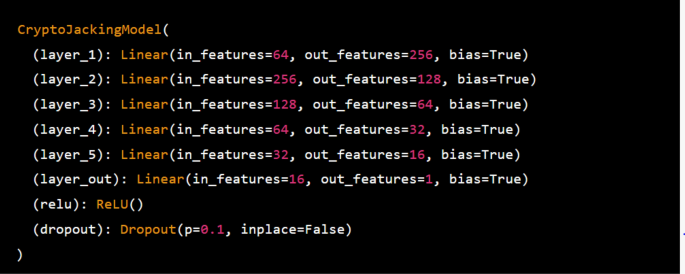
A deep learning approach for host-based cryptojacking malware detection
Variants of Crypto-Jacking Attacks and Their Detection Techniques

Cryptojacking - 5 Ways To Prevent Attacks

PDF] CoinPolice: Detecting Hidden Cryptojacking Attacks with Neural Networks

Full article: Cryptojacking injection: A paradigm shift to cryptocurrency- based web-centric internet attacks

The number of instances of the Coinhive miner scripts found using the

PDF] CoinPolice: Detecting Hidden Cryptojacking Attacks with Neural Networks
WR.1943-5452.0001265/asset/4d8d4969-3ab3-485d-a969-71e7768e3e7a/assets/images/large/figure2.jpg)
Review of Modeling Methodologies for Managing Water Distribution Security, Journal of Water Resources Planning and Management

Delay-CJ: A novel cryptojacking covert attack method based on delayed strategy and its detection - ScienceDirect

PSAK: A provably secure authenticated key agreement scheme based on extended Chebyshev chaotic maps for smart grid environments - Wang - 2023 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
de
por adulto (o preço varia de acordo com o tamanho do grupo)