The Hidden Threat to Your SecOps: Tampered Log Data
Por um escritor misterioso
Descrição
Log data plays a critical role in SecOps by providing insights into systems. This makes log data a popular target for cybercriminals.

Monthly Archive
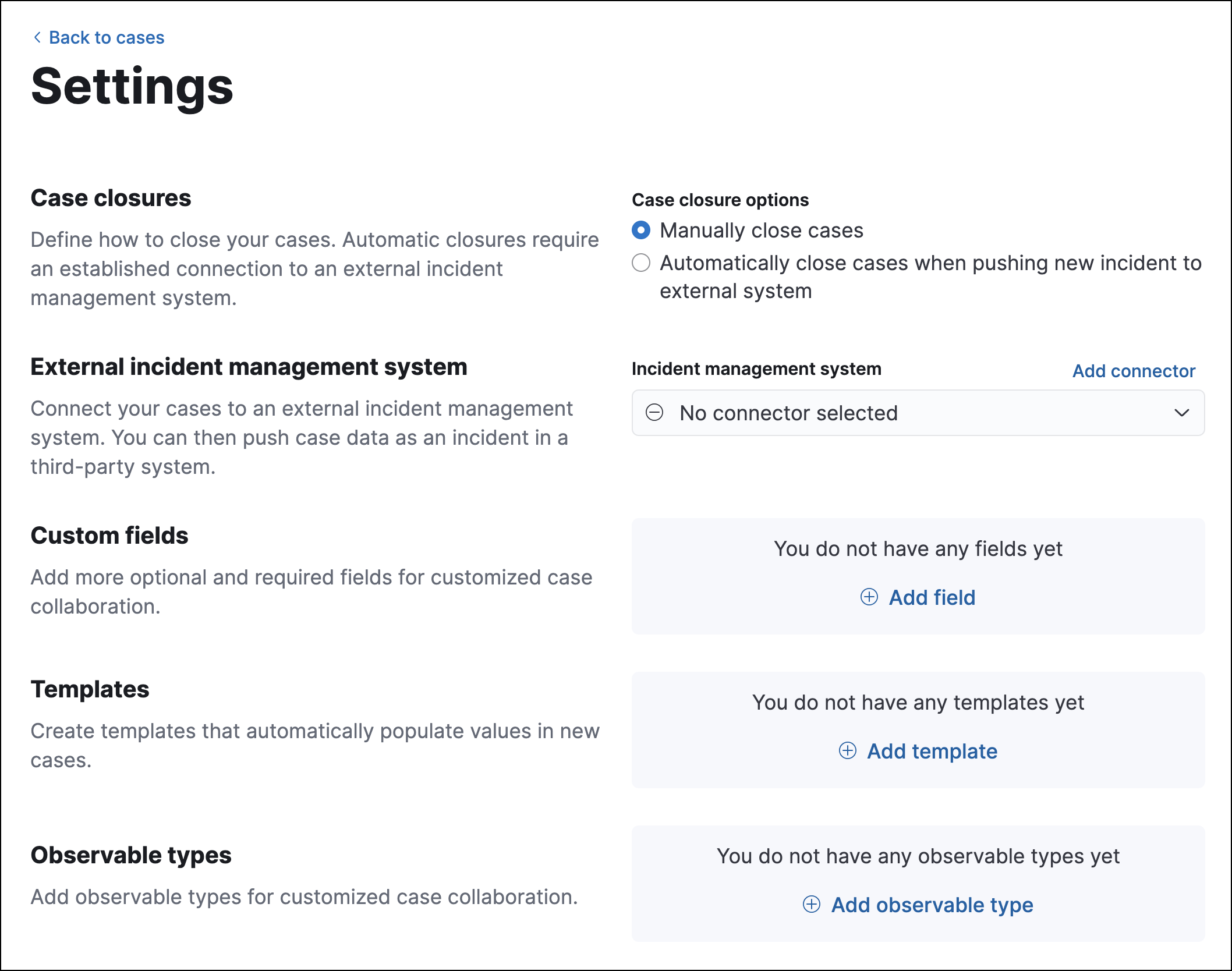
Configure external connections, Elastic Security Solution [8.11]

From GitHub to Account Takeover: Misconfigured Actions Place GCP & AWS Accounts at Risk - Rezonate
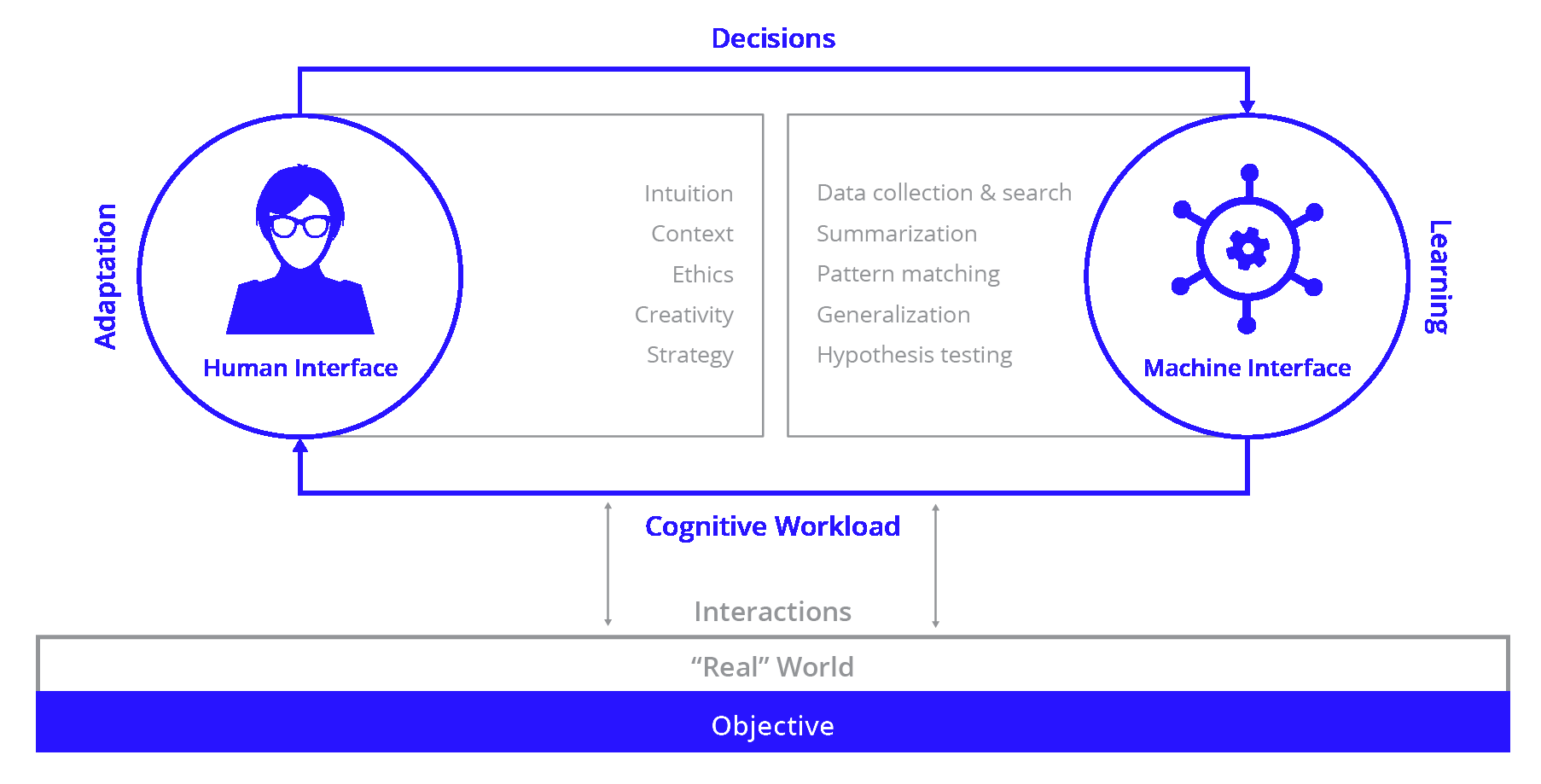
What Is Cyber Threat Hunting?

OWASP Top 10 LLM risks - what we learned

How to?! – ITSolutionDesign (Martin's technology notepad)
Threat-Hunting for Identity Threats in Snowflake

Brief: Threats from Retail Store-Based Intrusions
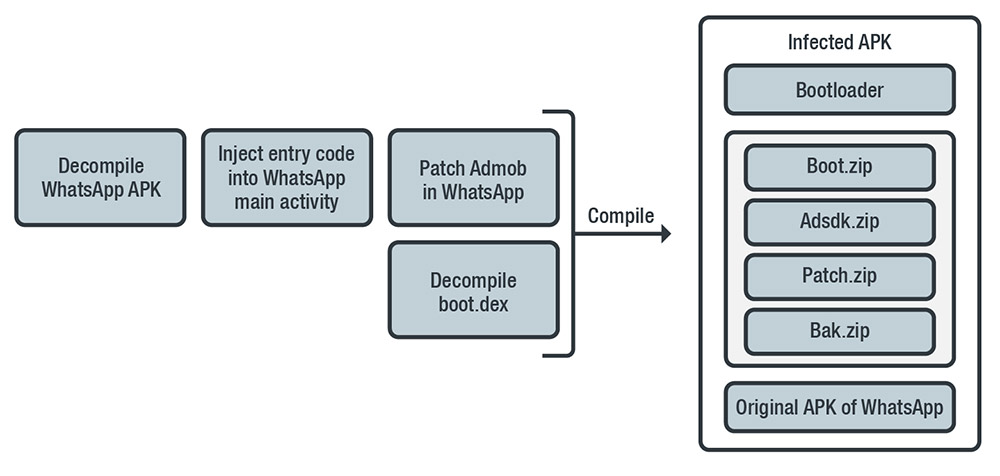
Review, Refocus, and Recalibrate: The 2019 Mobile Threat Landscape - Security Roundup

Threat-Hunting for Identity Threats in Snowflake

Beginners Guide to SAP Security: Why is it Important and How Does it Work?
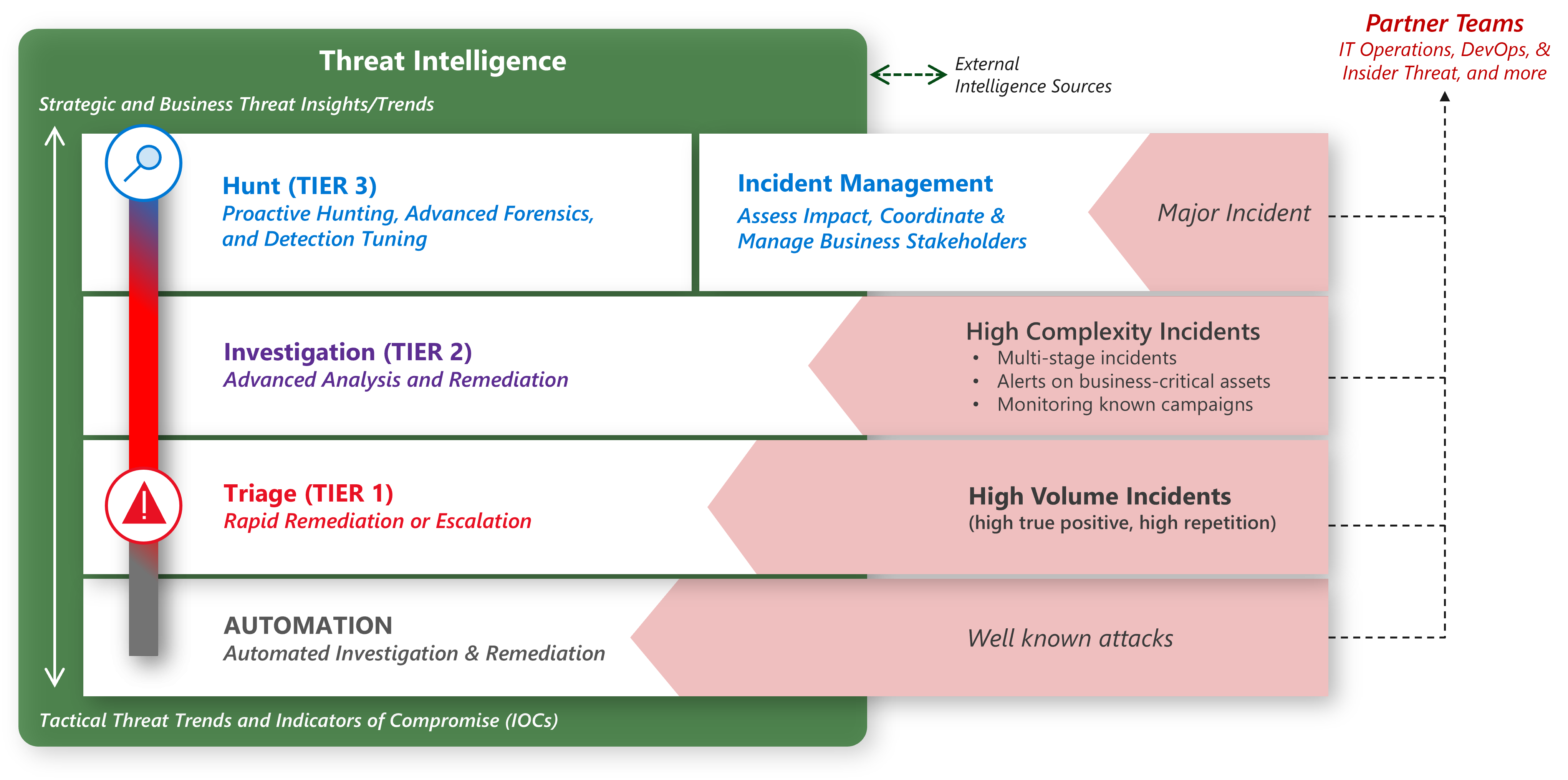
Security operations - Cloud Adoption Framework

Listen to Meanwhile in Security podcast
de
por adulto (o preço varia de acordo com o tamanho do grupo)