Vare Stealer - Malware removal instructions
Por um escritor misterioso
Descrição
Hackers Use Malicious NPM Packages To Steal Data in the IconBurst Supply Chain Attack - CPO Magazine

Lumar malware Removal Guide - How to remove Lumar Stealer malware
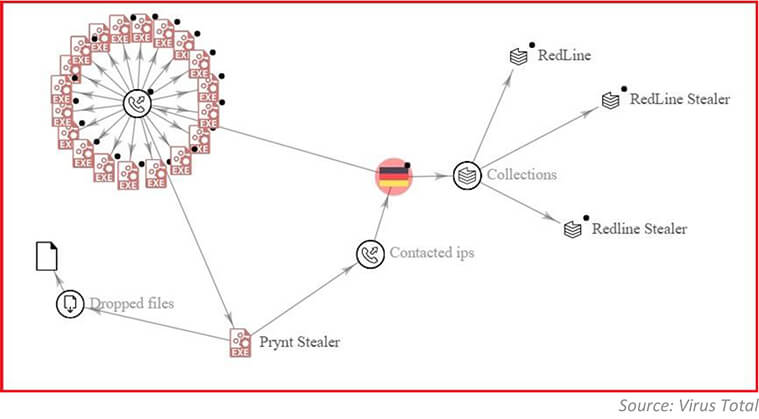
Infostealer Prynt Malware a Deep Dive into Its Process Injection Technique - CYFIRMA

Weird, Scary, and Annoying malware

The Battle for the World's Most Powerful Cyberweapon - The New York Times

Spyware, banking malware, smishing: do you know the main threats on mobile devices?

This figure represents the adaptation of the cyber kill chain model

PDF) DOTMUG: A Threat Model for Target Specific APT Attacks-Misusing Google Teachable Machine

Engineered Hemostatic Biomaterials for Sealing Wounds

Riskware: What It Is and How to Avoid It
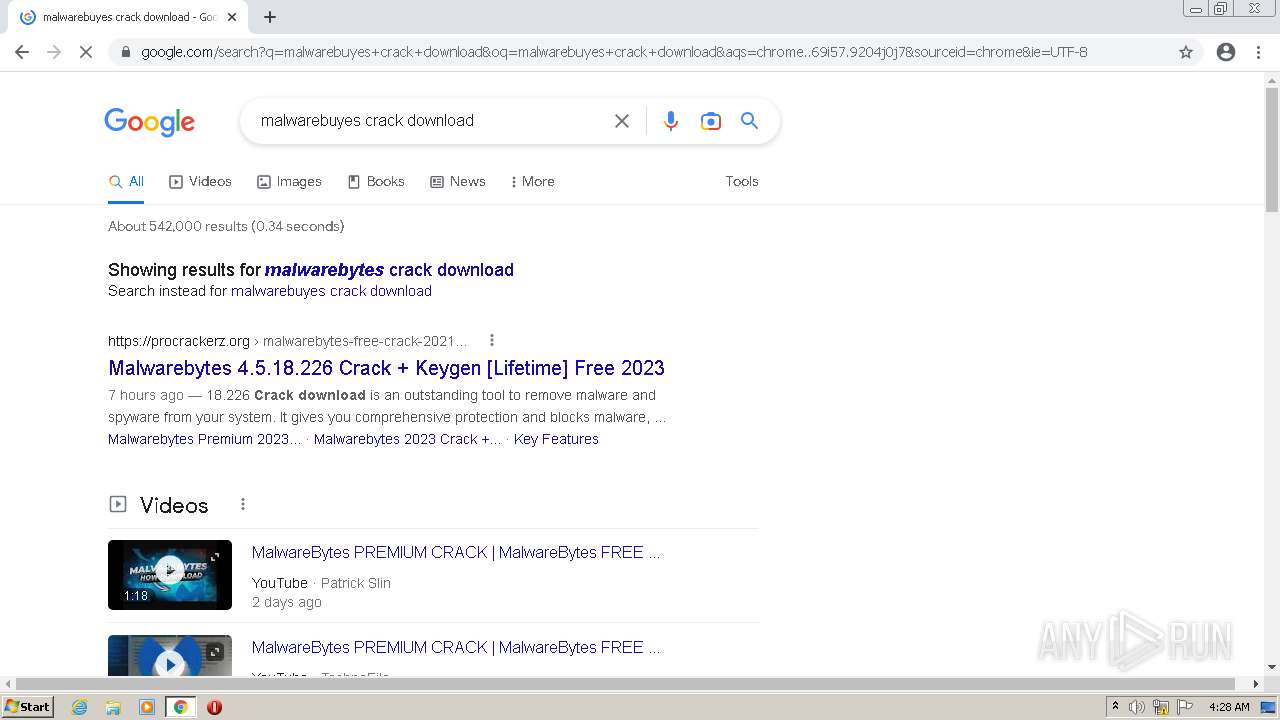
Malware analysis Malicious activity

Artificial intelligence for cybersecurity: Literature review and future research directions - ScienceDirect
de
por adulto (o preço varia de acordo com o tamanho do grupo)