SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Descrição
As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.

SILKLOADER: How Hackers Evade Detection

Types of Evasion Technique For IDS - GeeksforGeeks

Chinese Silkloader cyber attack tool falls into Russian hands

Evading AV with Veil-Evasion
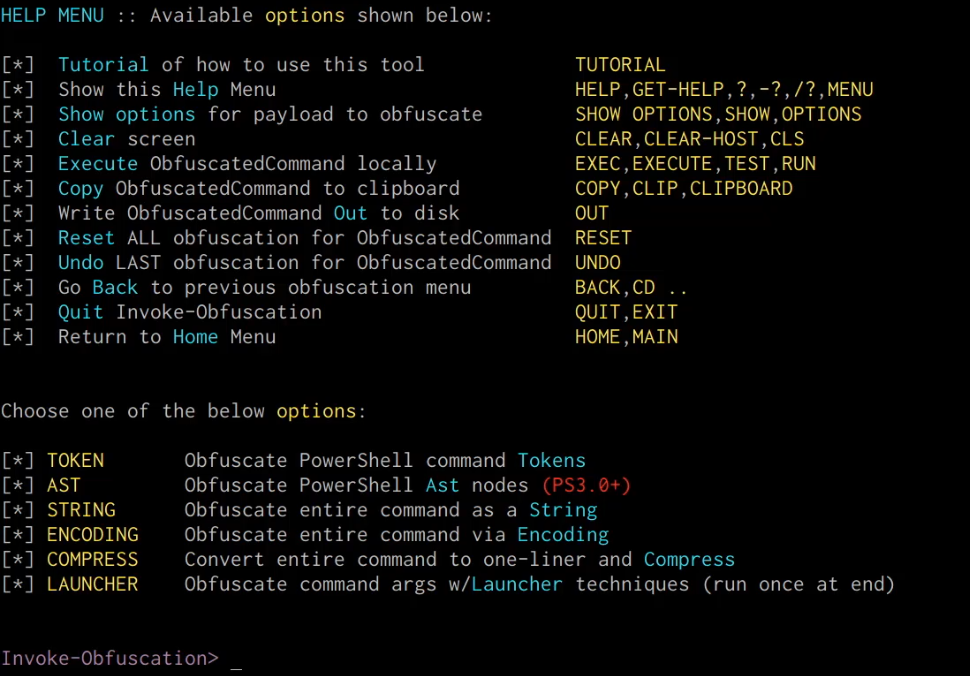
Windows Red Team Defense Evasion Techniques - HackerSploit Blog

Hackread - Latest Cybersecurity News, Press Releases & Technology Today

Cobalt Strike, Breaking Cybersecurity News

SILKLOADER: How Hackers Evade Detection

Evading AV with Veil-Evasion

How Hackers Are “Blending In” to Evade Detection
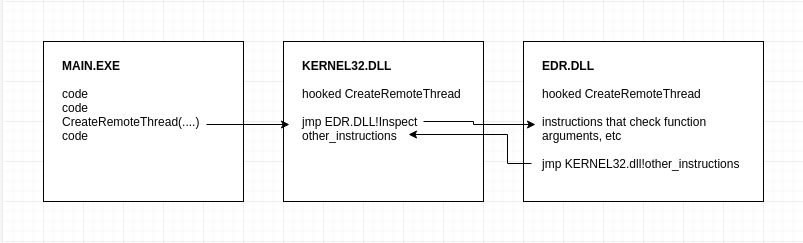
AV/EDR Evasion, Malware Development P-3

Telerik Government breach, Critical Outlook bug, LockBit threatens SpaceX

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA

Operation Soft Cell: Chinese Hackers Breach Middle East Telecom Providers : r/RedPacketSecurity
de
por adulto (o preço varia de acordo com o tamanho do grupo)