Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Complex 'NKAbuse' Malware Uses Blockchain to Hide on Linux, IoT

Endpoint Detection and Response, Free - What is EDR Security?

Security Orchestration Use Case: Automating Malware Analysis
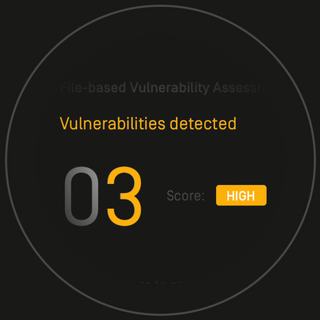
MetaDefender Cloud Advanced threat prevention and detection
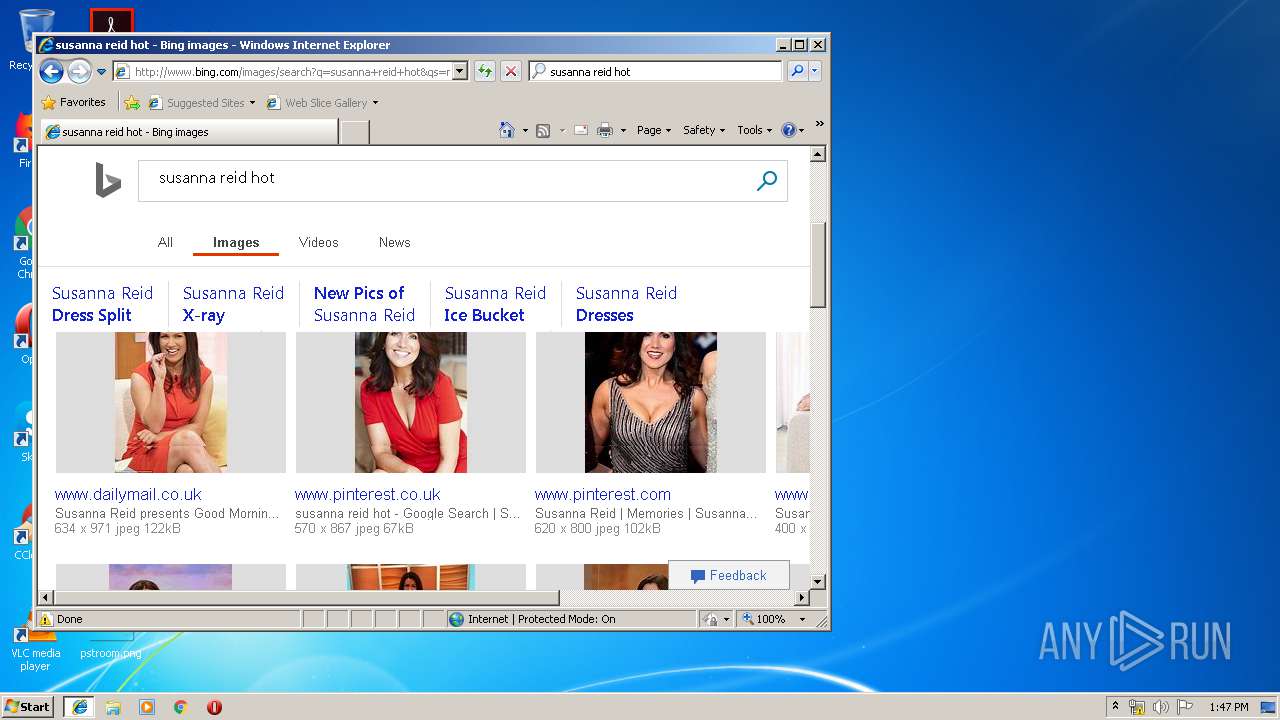
Malware analysis index.html Malicious activity

Endpoint Detection and Response, Free - What is EDR Security?
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware

Cybersecurity Search Engine

Mastering Malware Analysis

Free Cybersecurity Training and Career Development

What Is Malware Analysis? Definition, Types, Stages, and Best

MetaDefender Cloud Advanced threat prevention and detection

Malware Analysis - What is, Benefits & Types (Easily Explained)
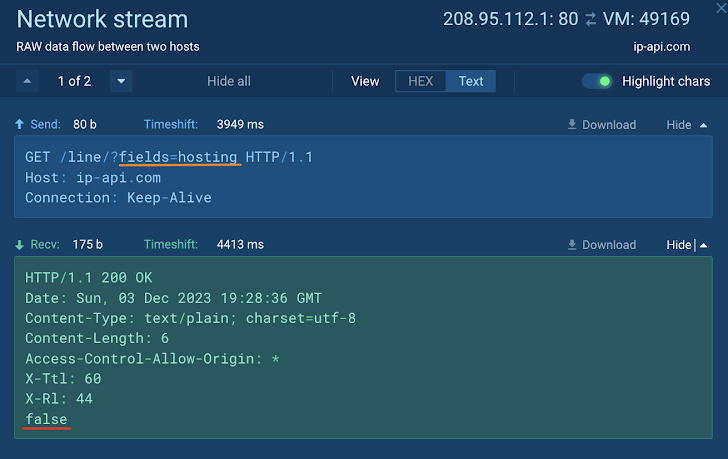
How to Analyze Malware's Network Traffic in A Sandbox
de
por adulto (o preço varia de acordo com o tamanho do grupo)




:max_bytes(150000):strip_icc()/the-owl-house-753dd85259994944b6ad5914100f0a7d.jpg)
