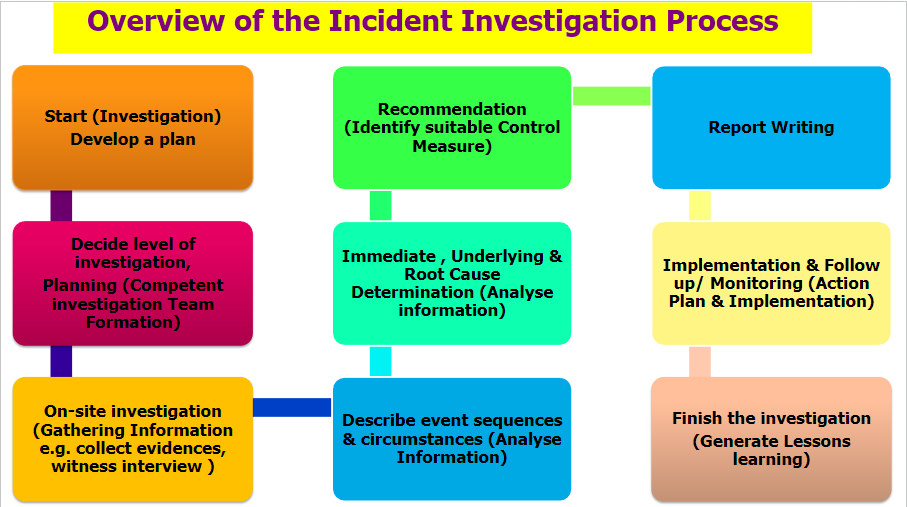
Using an Incident-Focused Model for Information Security Programs
Por um escritor misterioso
Descrição
[nodOrganizations attempt to prevent information security incidents by embedding tools in policies and practices across business functions. Because it is not possible to completely prevent security events, organizations must also include proven response practices as part of their security program. e:summary]
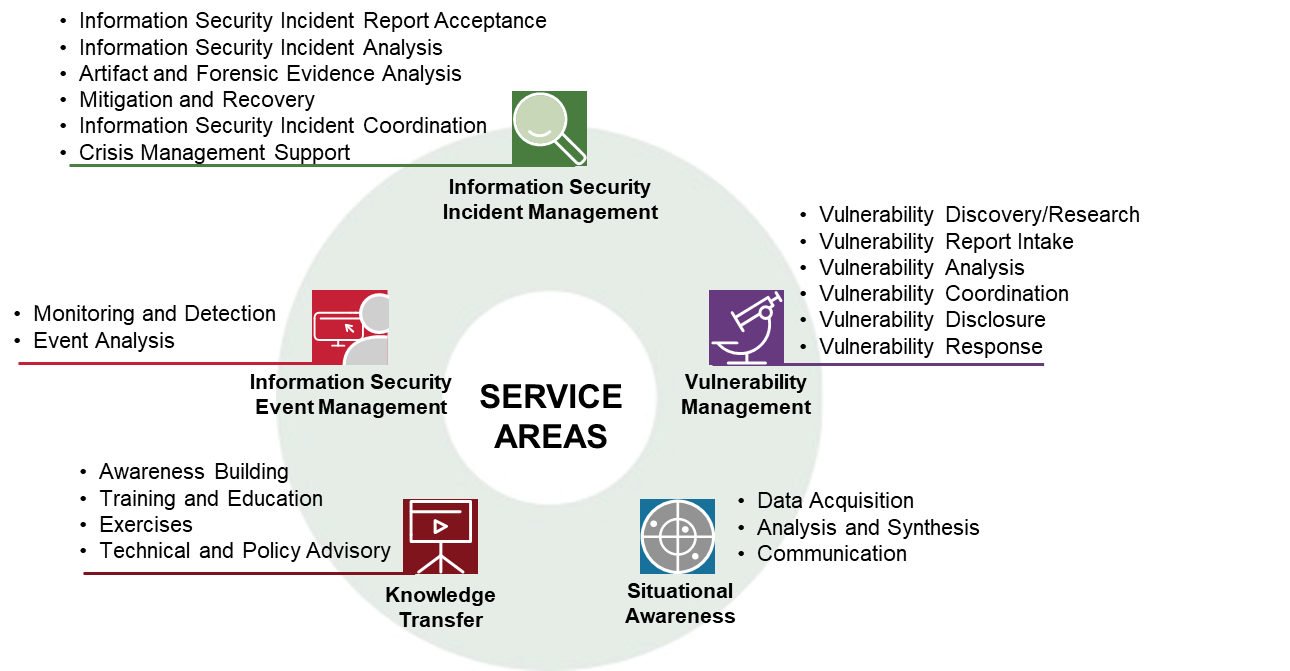
CSIRT Services Framework Version 2.1

Top 5 Most Common Incident Response Scenarios

What is Zero Trust Security? Principles of the Zero Trust Model
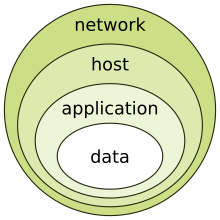
Information security - Wikipedia

Chapter 3 Cybersecurity Plans and Strategies, Establishing

CIS Critical Security Control 17: Incident Response and Management

How to Create a Cybersecurity Incident Response Plan - Hyperproof
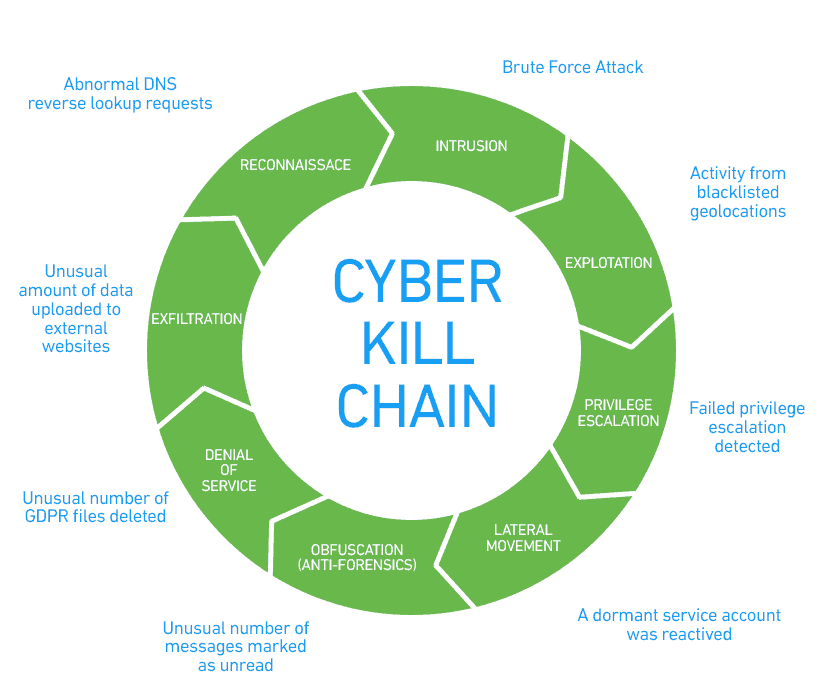
Cyber Kill Chain: Understanding and Mitigating Advanced Threats

Security Operations, SecOps
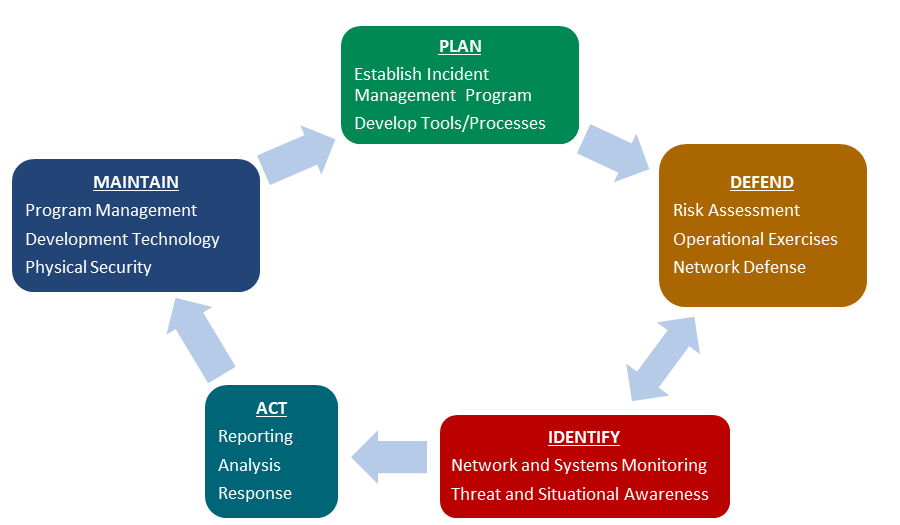
Top 5 Incident Management Issues

How to Create an Incident Response Plan (Detailed Guide)

How to apply incident response for SaaS? - Polymer

ECIH Certification: Master Incident Handling in Cybersecurity

The complete information security incident management process

How to Create an Incident Response Plan (Detailed Guide)
de
por adulto (o preço varia de acordo com o tamanho do grupo)