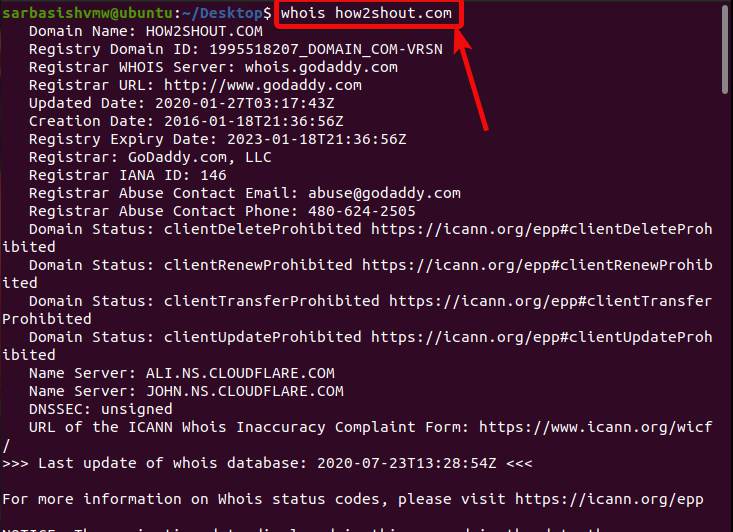
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Descrição
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

How did I create hacking rig for ethical hacking. Based on VMware with Tesla M60. #infosec #hacking #pentest #pentesting #redteam #hackthebox #tryhackme #linux4hackers #ctf #kali #parrotos #linux #godaddy #linux4hackers – Tips and
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Hackers Secure Wildly Popular Video Game at H1-407

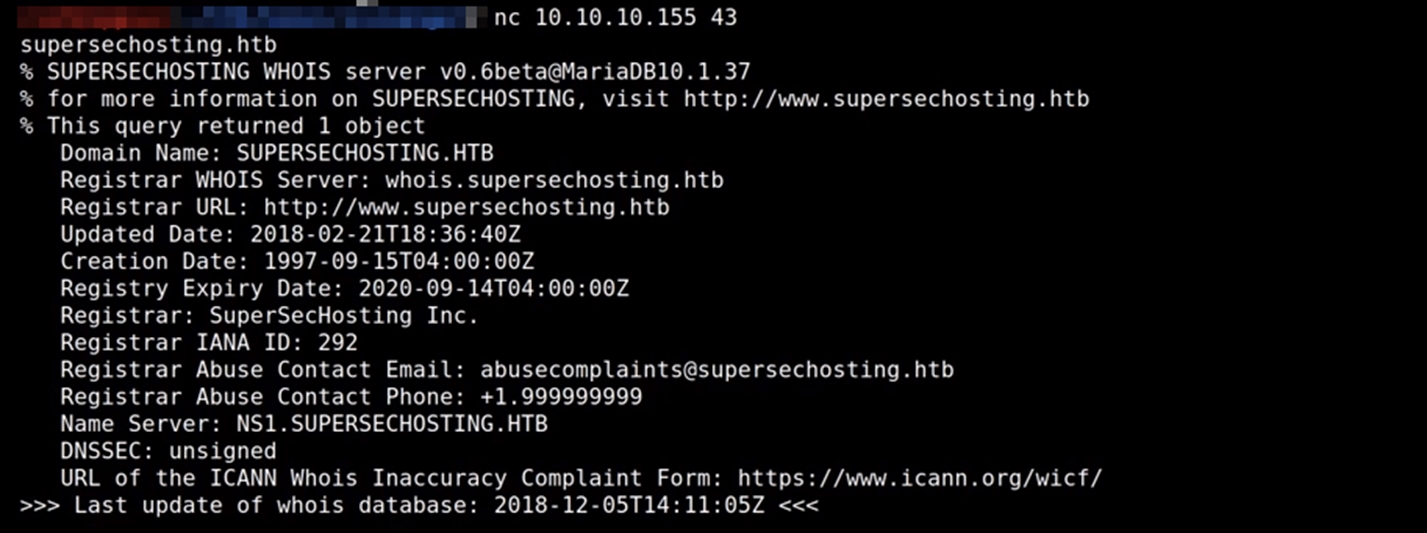
Tips for Investigating Cybercrime Infrastructure

Infrastructure Hacking: DNS Protocol II » Hacking Lethani

Should you use Let's Encrypt for internal hostnames? – Terence Eden's Blog

7 powerful pentesting tools (& why you should stop pedestalizing them)

Cyber Security & Ethical Hacking - Whois ( “who owns a domain?”)

tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS

N. Korean Hackers Distribute Trojanized CyberLink Software in Supply Chain Attack
Ronin Hack: North Korea's Lazarus Behind $540 Million Axe Infinity Breach
de
por adulto (o preço varia de acordo com o tamanho do grupo)