Cybercriminals turn Facebook's security features into exploits
Por um escritor misterioso
Descrição

How To Hack Facebook In 60 Seconds

Stolen credentials increasingly empower the cybercrime underground
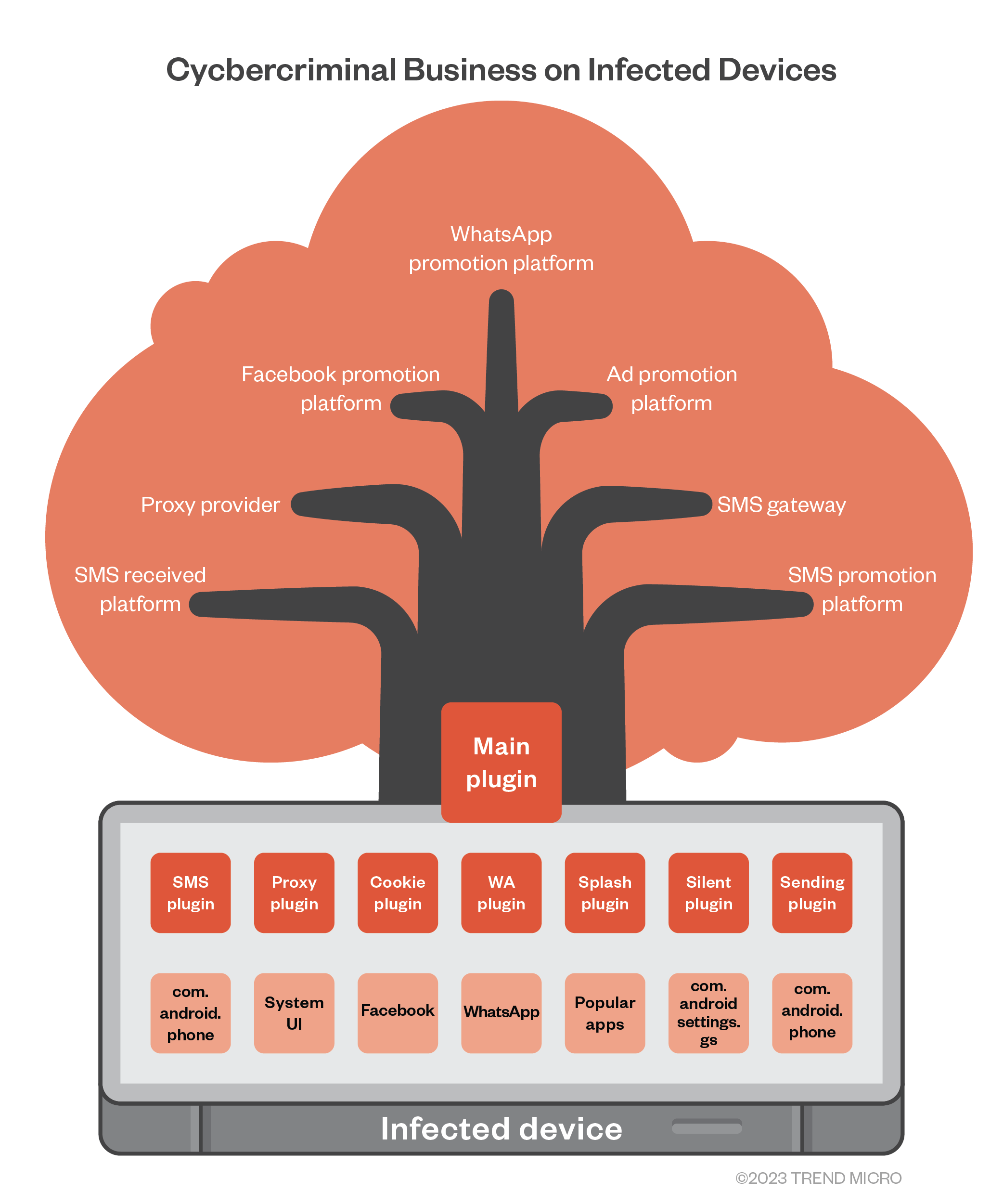
Lemon Group's Cybercriminal Businesses Built on Preinfected Devices

Cybercriminals turn Facebook's security features into exploits

Why should cybersecurity become top priority for SMEs - SME News

How your business can prevent 6 types of cybercrime

Cybercriminals turn Facebook's security features into exploits

Exploit-as-a-service: Cybercriminals exploring potential of leasing out zero-day vulnerabilities

Cybersecurity in Education: What Teachers, Parents and Students Should Know

What to do if someone tries to hack your Facebook or Instagram account

Attack campaign uses PHP-based infostealer to target Facebook business accounts

Facebook scammers exploit your intention to hack friends' account

Businesses braced for bout of regulation on cyber security

Beware of Meta's Threads: experts warn of privacy concerns and opportunistic scams
de
por adulto (o preço varia de acordo com o tamanho do grupo)