DigitalResidue's Forensics: Malware Incident Response pt. 2. (Collecting Volatile and Non-Volatile data)
Por um escritor misterioso
Descrição
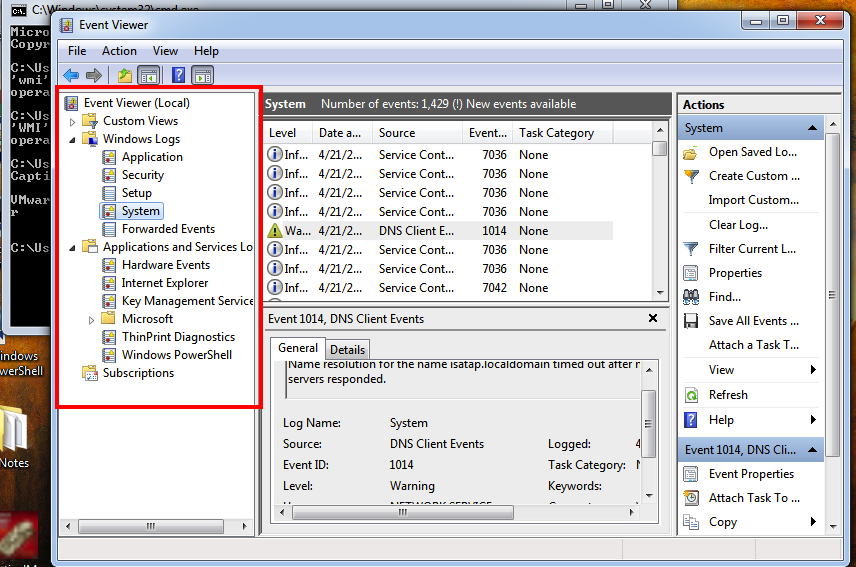
DigitalResidue's Forensics: Malware Incident Response pt. 2. (Collecting Volatile and Non-Volatile data)

DigitalResidue's Forensics

17.2- Performing Incident Response - Part 2 (Managing Data Sources for Incident Response Lab)

Memory Forensics for Incident Response

Analyzing Memory Dumps — R2D2 Malware, by ka1d0
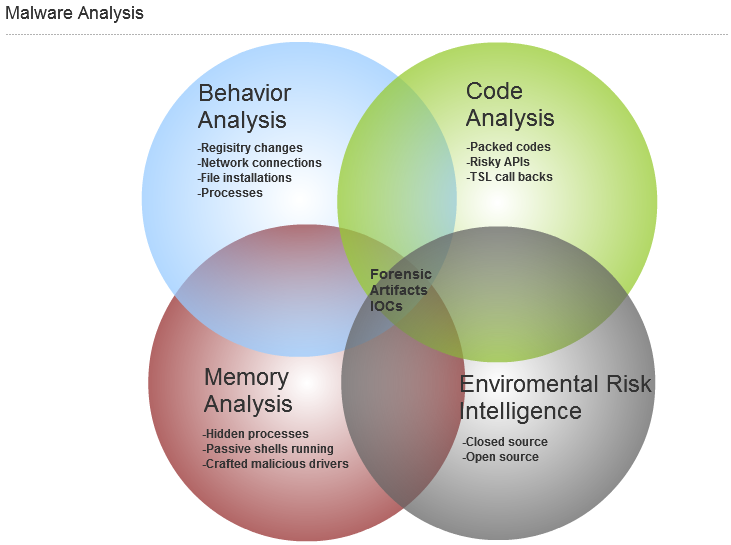
SANS Digital Forensics and Incident Response Blog, Four Focus Areas of Malware Analysis

computer forensics:Initial Response & Volatile Data Collection from Windows system

Distributed forensics and incident response in the enterprise - ScienceDirect

Malware Forensics for Volatile and Nonvolatile Memory in Mobile Devices

Incident Response: Methodology and Case Study – Fire Hunter's Blog
de
por adulto (o preço varia de acordo com o tamanho do grupo)







