Collecting XSS Subreddit Payloads
Por um escritor misterioso
Descrição
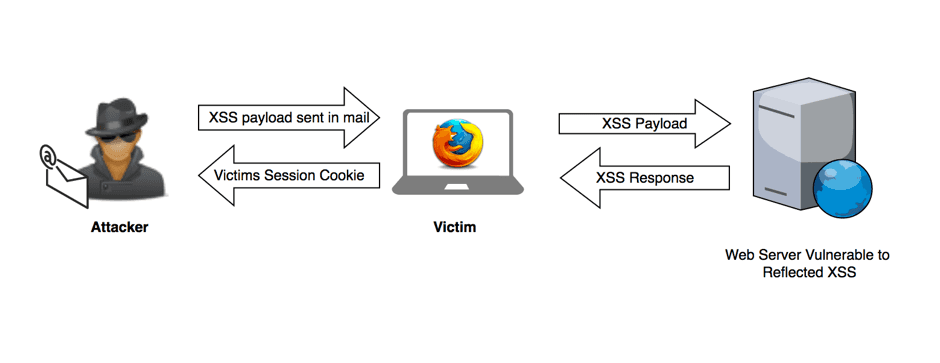
Having a good collection of Cross-Site Scripting (XSS) payloads is useful when you want to thoroughly test a web site’s ability to defend itself from being exploited. In most cases you can just run any one or more open source and/or commercial scanning tools to test your web site.

Neatly bypassing Content Security Policy. Why 'unsafe-inline' is almost always a full-fledged XSS : r/netsec

Reddit Hit by Cyberattack that Allowed Hackers to Steal Source Code
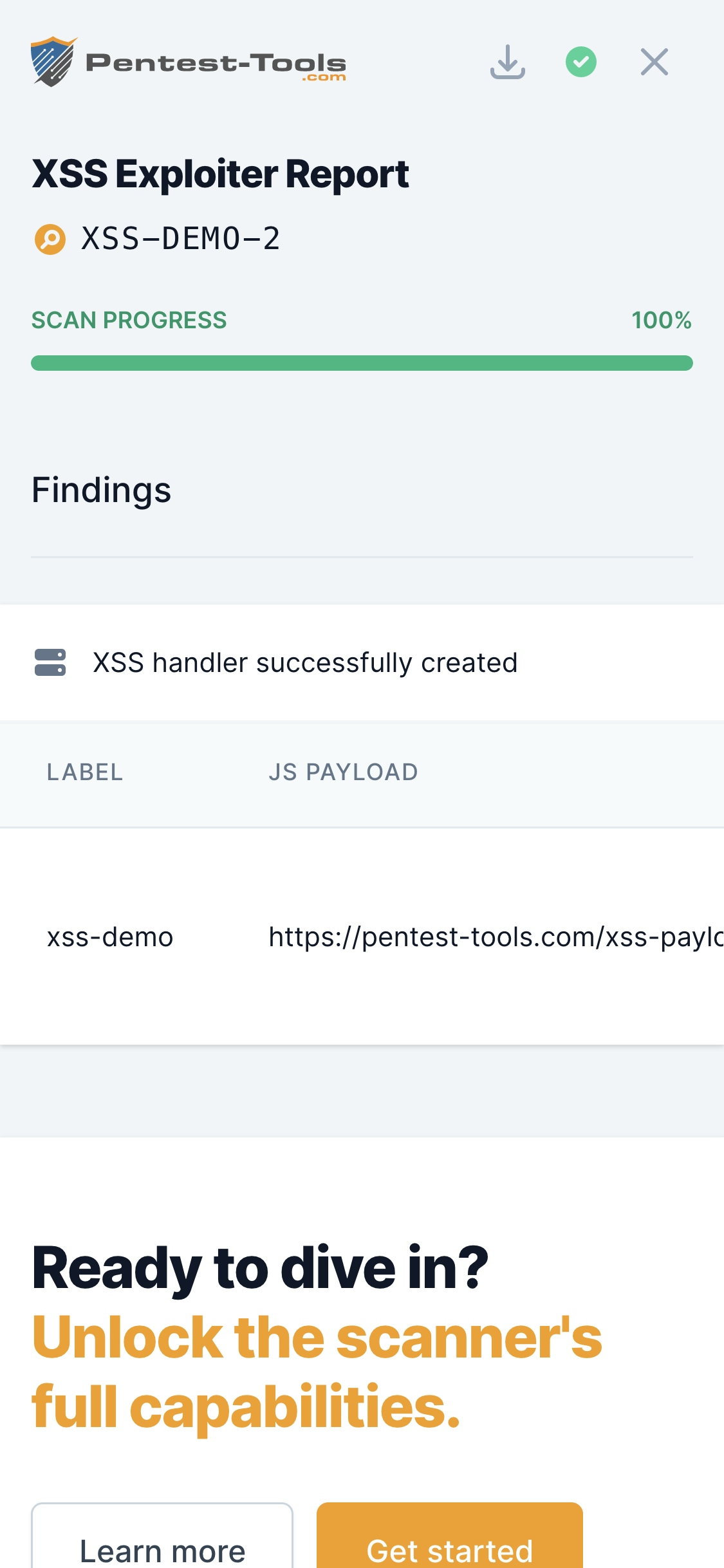
XSS Exploiter - Exploit Cross Site Scripting
GitHub - foospidy/payloads: Git All the Payloads! A collection of web attack payloads.
🔓 Unlocking the power of the ChatGPT revolution: 100 💥 innovative use-cases to try before you 💔 are fired 🔥, by Florin Badita
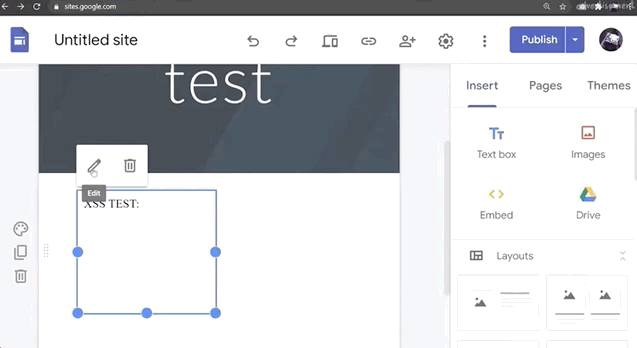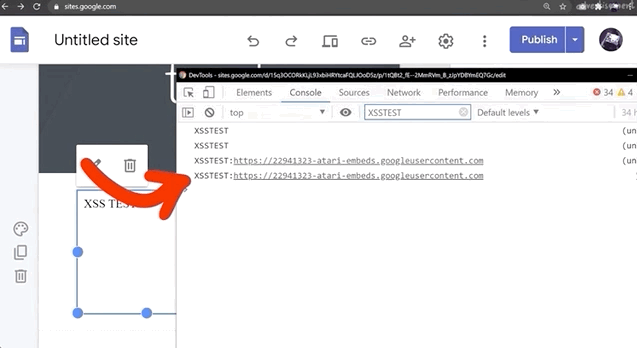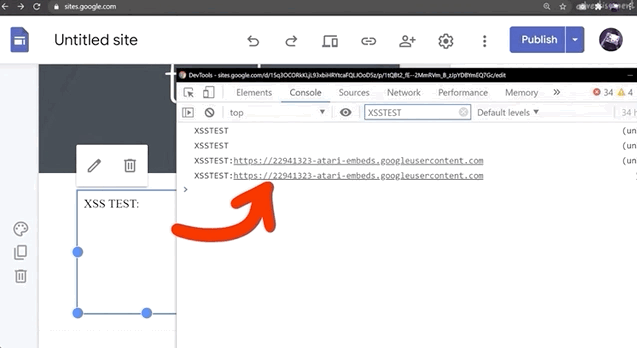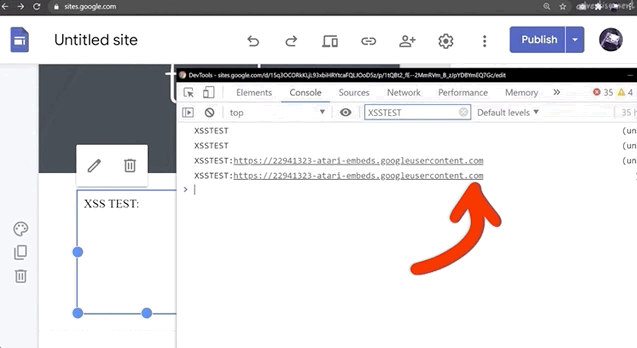
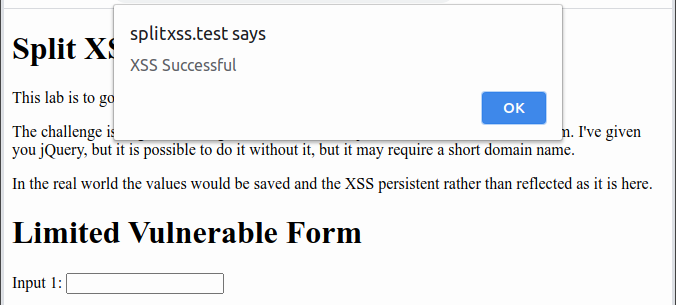
Do NOT use alert(1) in XSS

XSS Hunting using Google Dorking - OCD Tech
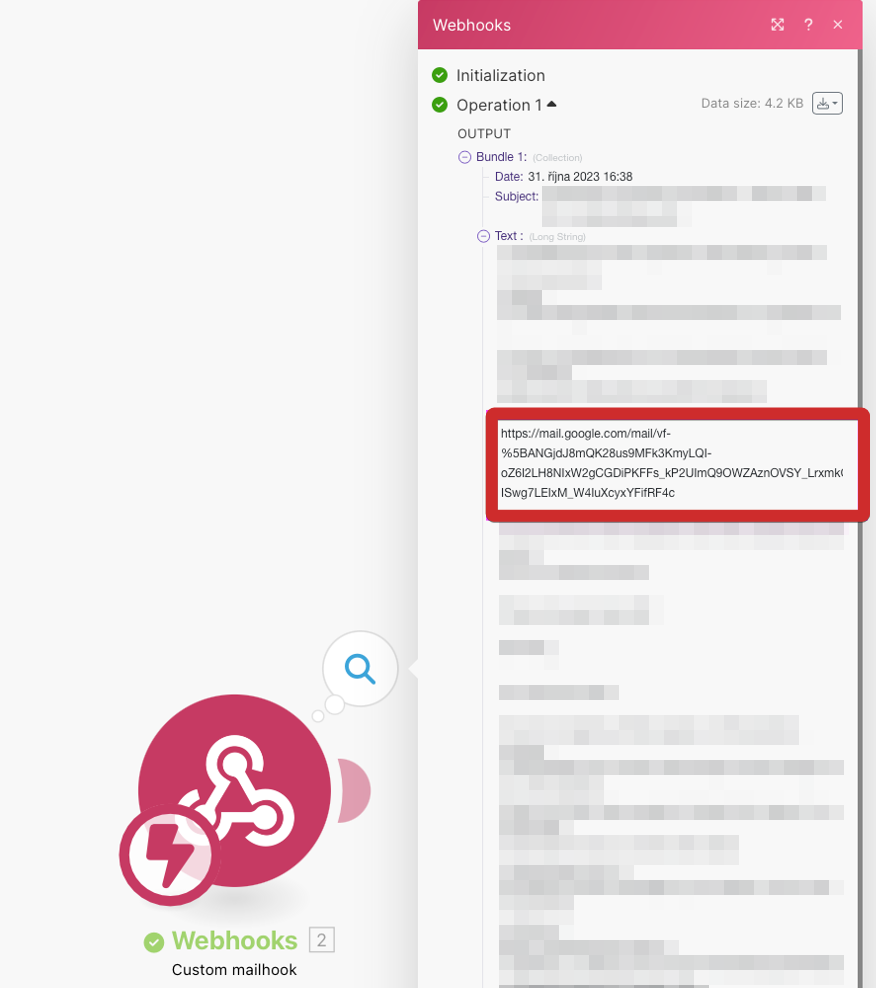
Webhooks

RedditC2 - Abusing Reddit API To Host The C2 Traffic, Since Most Of The Blue-Team Members Use Reddit, It Might Be A Great Way To Make The Traffic Look Legit

Truffle Security relaunches XSS Hunter tool with new features

What is a Cross-Site Scripting (XSS) attack: Definition & Examples

How to Make Your NodeJS Application Secure (24 Best Security Tips )
de
por adulto (o preço varia de acordo com o tamanho do grupo)