Bluejacking vs Bluesnarfing: Exploring Bluetooth Hacking Variations.
Por um escritor misterioso
Descrição
Discover the potential security risks of Bluetooth technology, including various types of attacks like bluejacking, bluesnarfing, bluebugging
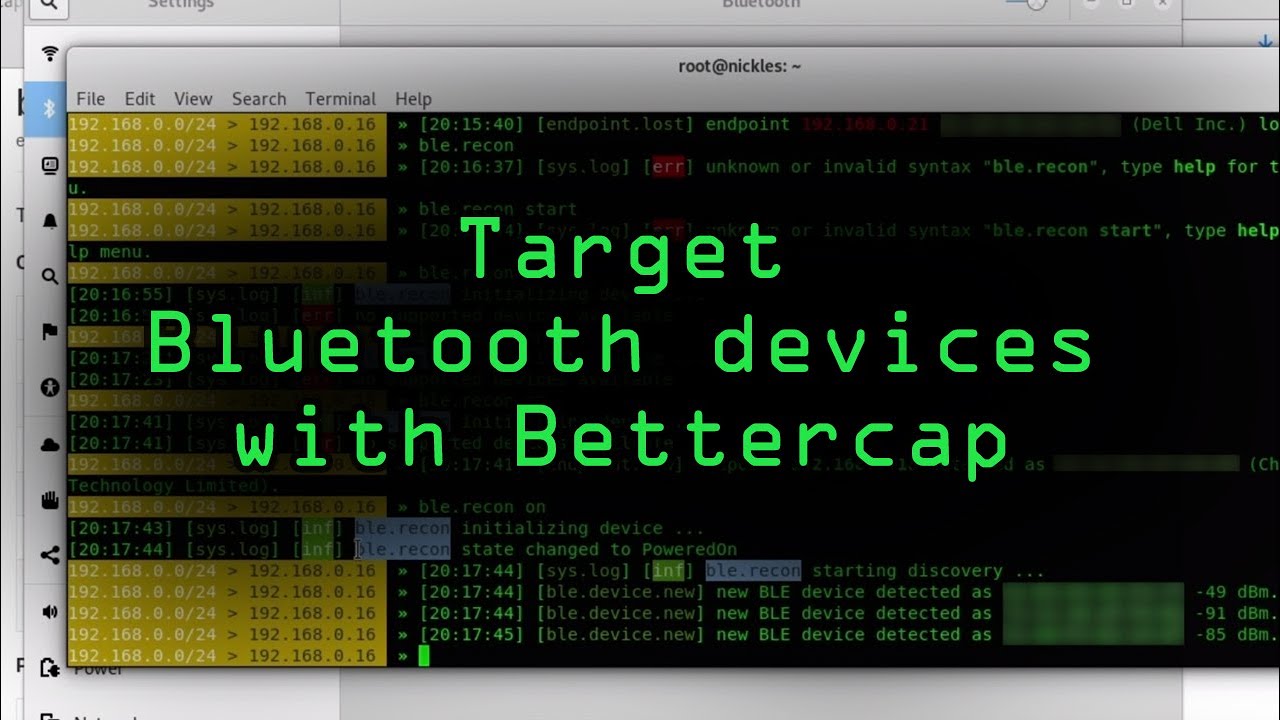
How to Target Bluetooth Devices with Bettercap « Null Byte :: WonderHowTo

What is bluebugging? Know all about the vulnerability of Bluetooth-enabled devices

Top 25 Cyber & Hacking Terms Summarised
GitHub - StealthIQ/Bluestrike: Bluestrike: CLI tool to hack Bluetooth devices through speaker jamming, traffic spoofing & device hijacking (In the making)

Diferencias entre los principales ataques por bluetooth: Bluesnarfing, Bluejacking y Bluebugging - CNET Technology Systems

PDF) Security Vulnerabilities in Bluetooth Technology as Used in IoT
Introduction to How Bluetooth Surveillance Works

Bluebugging: do you know about this Bluetooth security risk?

Blue Jacking

Module 7: Bluejacking
Bluejacking vs Bluesnarfing: Decoding Common Word Mix-Ups
de
por adulto (o preço varia de acordo com o tamanho do grupo)







