Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
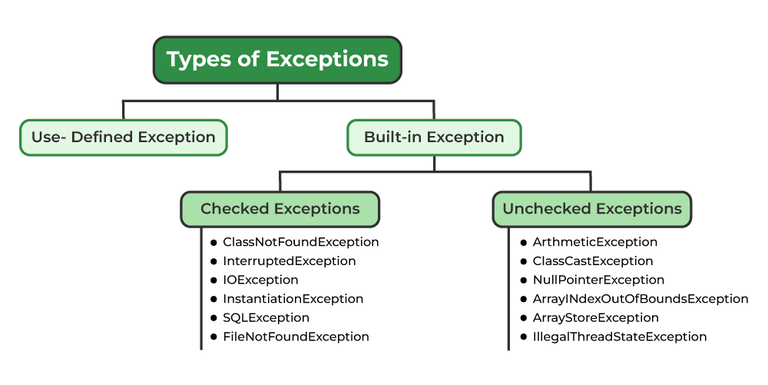
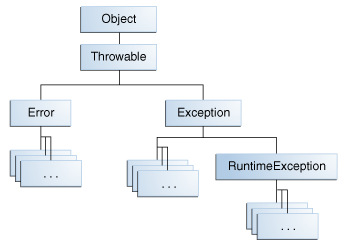
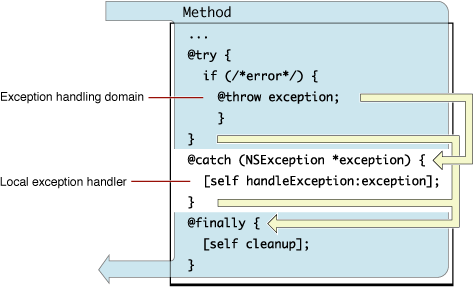
Descrição
In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.
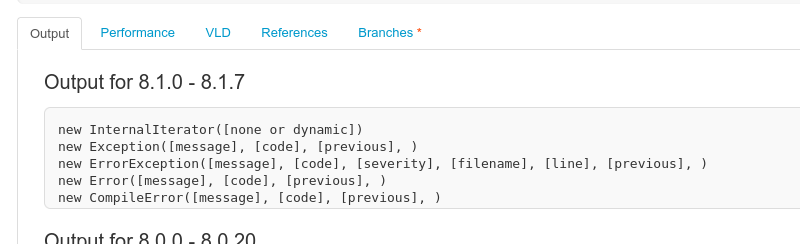
PHP - RCE abusing object creation: new $_GET[a]($_GET[b

How to protect, prevent and mitigate buffer overflow attacks

What is an Integer Overflow Attack (with Examples)?

Changing Spring Boot Env Properties at Runtime

CVE-2022-22965 (SpringShell): RCE Vulnerability Analysis and
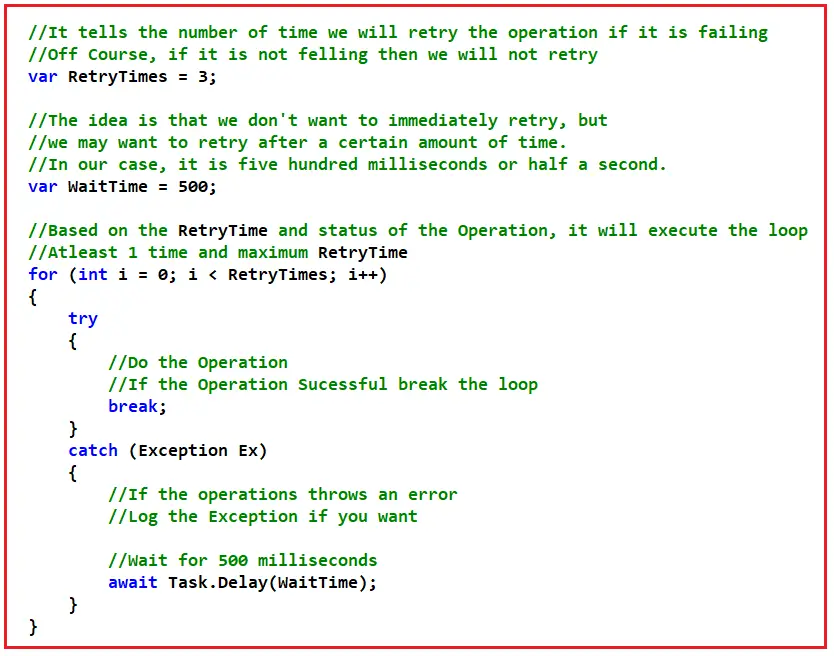
Retry Pattern in C# with Examples - Dot Net Tutorials
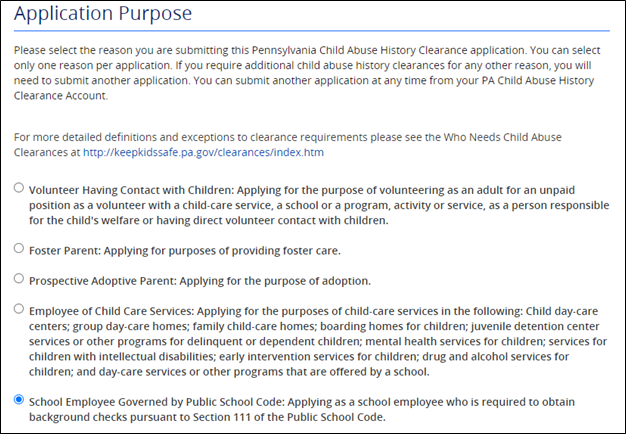
Instructions for Obtaining a Pennsylvania Child Abuse History

What is a Buffer Overflow Attack Types and Prevention Methods
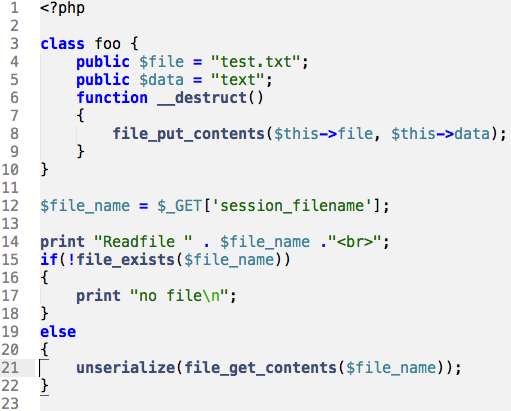
Remote code execution via PHP [Unserialize]

Secure Your AWS EC2 IMDS - Tenable Cloud Security
de
por adulto (o preço varia de acordo com o tamanho do grupo)